TECHNICAL REPORT
| Grantee |
Dr. Muhammad Yousaf
|
| Project Title | Deployment of Collaborative Modern HoneyNet to improve Regional Cybersecurity Landscape (CMoHN) |
| Amount Awarded | AUD 29,300 |
| Dates covered by this report: | 2017-11-20 to 2018-04-20 |
| Report submission date | 2018-07-20 |
| Economies where project was implemented | Pakistan |
| Project leader name |
Dr. Muhammad Yousaf
|
| Project Team |
Mr. Tariq Saraj
[email protected]
Mr. Sohaib Jamil
[email protected]
|
| Partner organization | 1) Faculty of Computing, Riphah International University, Islamabad, 2) Associated Press of Pakistan, 3) National Engineering and Scientific Commission |
Project Summary
Firewalls, IDS/IPS, SIEM Solutions, Anti-virus, and other such information security products have been efficient to detect and prevent the known cybersecurity attacks. However, these devices have the built-in limitation in identifying new attack strategies and mechanisms. Along with these security products, honeynets are an integral part of the emerging secure network infrastructure of the modern age enterprises. Honeypot concept has been around for many years for engaging and learning about the hacker's attack strategies. This project aimed to achieve the following objectives: To establish core competency in deployment and integration of different honeypots and honeynets, To establish core competency in designing new honeypots for countering the current cyber-attacks, To establish an Internal Research Honeynet, To establish an External Production Honeynet, To establish a multi-site collaborative Honeynet Network, To connect with other honeynets in the region to form a regional collaborative honeynet network, To promote R&D activities around the secure network infrastructures by publishing our work in the reputed international conferences and journals, To promote secure network infrastructure practices by conducting community awareness seminars. In order to achieve the objectives of the project, we established two teams. Team-one consisted of research engineers that got expertise in deploying and integration of different honeypots and honeynets. This team successfully deployed the internal research and a couple of external production honeynets. Team-two consisted of the graduate research students who voluntarily took interest in the project activities and contributed in designing new honeypots for embedded Linux devices to counter the attacks against the Internet of Things (IoT) devices and establishing the interface between honeynet and the other security devices like firewalls. With our deployed honeypots and honeynets at a number of locations, we are now able to observe thousands of cyber-attacks daily on our sites. This is helping us to identify the extent and variety of the attacks being faced by the organizations in this region.
Table of contents
- Project factsheet information
- Background and justification
- Project Implementation
- Project Evaluation
- Gender Equality and Inclusion
- Project Communication Strategy
- Recommendations and Use of Findings
- Bibliography
Background and Justification
With the emergence of the connected economies using large-scale cloud computing infrastructures and the increasing number of Internet of Things (IoT) devices, the exploitation of the information systems through cyber-attacks is getting serious day by day. With the sophistication in the defense mechanisms, the attack sophistication is also increasing. Although security professionals and vendors of the information security related products, always claim to have designed state of the art security controls, however, still at the regular intervals, the news is hit with some new security exploits and cyber-attacks.
Although Firewalls, IDS/IPS (Intrusion Detection/Prevention Systems), SIEM (Security Information and Event Management) Solutions, Anti-virus, and other such information security products have been efficient to detect and prevent the known cybersecurity attacks, however, these devices have a built-in limitation in identifying the new attack strategies and mechanisms. Honeypot concept has been around since many years for engaging and learning about the hacker's attack strategies (Mokube, Iyatiti, & Adams, 2007), (Spitzner & Lance, 2003), (Zhang, Feng, Zhou, Qin, & Liu, 2003). These honeypots have following distinct advantages over other security controls and products.
- They engage the attacker in a decoy system thus wasting the hacker's time at one side and on the other side alarming the security professionals about the prevailing attack danger.
- This provides security professionals ample time to become in the fire-fighting mode and devise the defense mechanisms against the attack.
- They observe the attack techniques and patterns and help vendors to improve their security products.
For different types of security attacks, we need to design different honeypots. Normally, several honeypots are deployed in a network and all of them are connected to form a Honeynet (Spitzner & Lance, 2003). These honeynets gather information from different honeypots to form a collective cybersecurity intelligence. These honeynets can be established at both internal and external sides of the network to counter the internal as well as external attacks.
Many organizations want to know that whether they have been a victim of a targeted attack or of some random epidemic attack. For this purpose, they need to see that whether the other same type of organizations have also been hit by the same attacks or not. It provides the security professionals with the regional cybersecurity situational awareness. In order to achieve this objective in real-time, there has been a growing trend to establish the collaborative regional honeynets. This project aims to establish such a Collaborative Modern HoneyNet (CMoHN).
Although there exist many experimental isolated deployments of the honeypots and the honeynets, however, these deployments do not establish a real-time regional cybersecurity situation awareness. There is a need to convert these isolated deployments into a regional collaborative cybersecurity community by connecting different honeynets situated in many different networks. This will help to identify the targeted attacks and the random attacks.
Considering the cyber-attacks diversity, the number of available honeypots are very limited. There is a need to do more work on this area and help the community by designing new honeypots for countering the evolving cybersecurity attack techniques. We cannot counter the exploit designed in the year 2018 with the honeypot designed in the year 2008. There will always be a need to evolve the honeypots with the new attack detection and tracking techniques.
There are two types of honeypots. One is the Production honeypots and the other is the Research honeypots. As the name suggests, the research honeypots are hosted in the research institutes. One such example is the Honeynet Project that was internally deployed in the Georgia Institute of Technology, USA in 2004. Our proposed project will initially work along the same lines by establishing an internal research honeynet. However, later on, the proposed project will be expanded towards the external network side, multi-site and then towards the regional collaborative honeynet deployment.
Project Implementation
Problem Statement:
Firewalls, IDS/IPS, SIEM Solutions, Anti-virus, and other such information security products have been efficient to detect and prevent the known cybersecurity attacks, however, these devices have the built-in limitation in identifying new attack strategies and mechanisms. We believe that along with these security products, honeynets are an integral part of the emerging secure network infrastructure architecture of the modern age enterprises. Honeypot concept has been around for many years for engaging and learning about the hacker's attack strategies. As mentioned earlier, this project intends to contribute in two distinct areas:
- Establishment of the regional collaborative honeynet to improve the situational cybersecurity awareness
- Expansion of the new honeypots to counter the new evolving cyber attacks
Project Objectives:
Collaborative Modern Honeynet (CMoHN) project aims to achieve the following objectives:
- To establish core competency in deployment and integration of different honeynets.
- To establish core competency in designing new honeypots for countering the current cyber-attacks.
- To establish an Internal Research Honeynet.
- To establish an External Production Honeynet.
- To establish a multi-site collaborative Honeynet Network.
- To connect with other honeynets in the region to form a regional collaborative honeynet network.
- To promote R&D activities around the secure network infrastructures by publishing out work in the reputed international conferences and journals.
- To promote secure network infrastructure practices by conducting community awareness seminars.
Work Conducted:
In order to achieve the first two objectives of the project, we developed two teams. Team-one consisted of two research engineers that got expertise in deploying and integration of different honeypots and honeynets. This team successfully deployed the internal research honeynet and the external production honeynet. Team one also developed a collaborative honeynet client and server for the communication between different honeynets. Moreover, this team also conducted the testing of the deployed honeynet. This testing was conducted from two different perspectives; one is from the attacker’s perspective through which we launched different cybersecurity attacks on our internal research honeynet and observed that how attacker sees and interact with the deployed honeypots. From the other perspective i.e. from the defense side perspective, we observed that how the defense team sees the attack activities.
Team-two consisted of the graduate research students who voluntarily took interest in the project activities and contributed in designing new honeypots for embedded Linux devices to counter the attacks against the Internet of Things (IoT) devices and establishing the interface between honeynet and the other security devices like firewalls. This interfacing links the detective and preventive devices with each other to create more effective cybersecurity ecosystem. Figure-01 depicts an abstract structure of the project components.
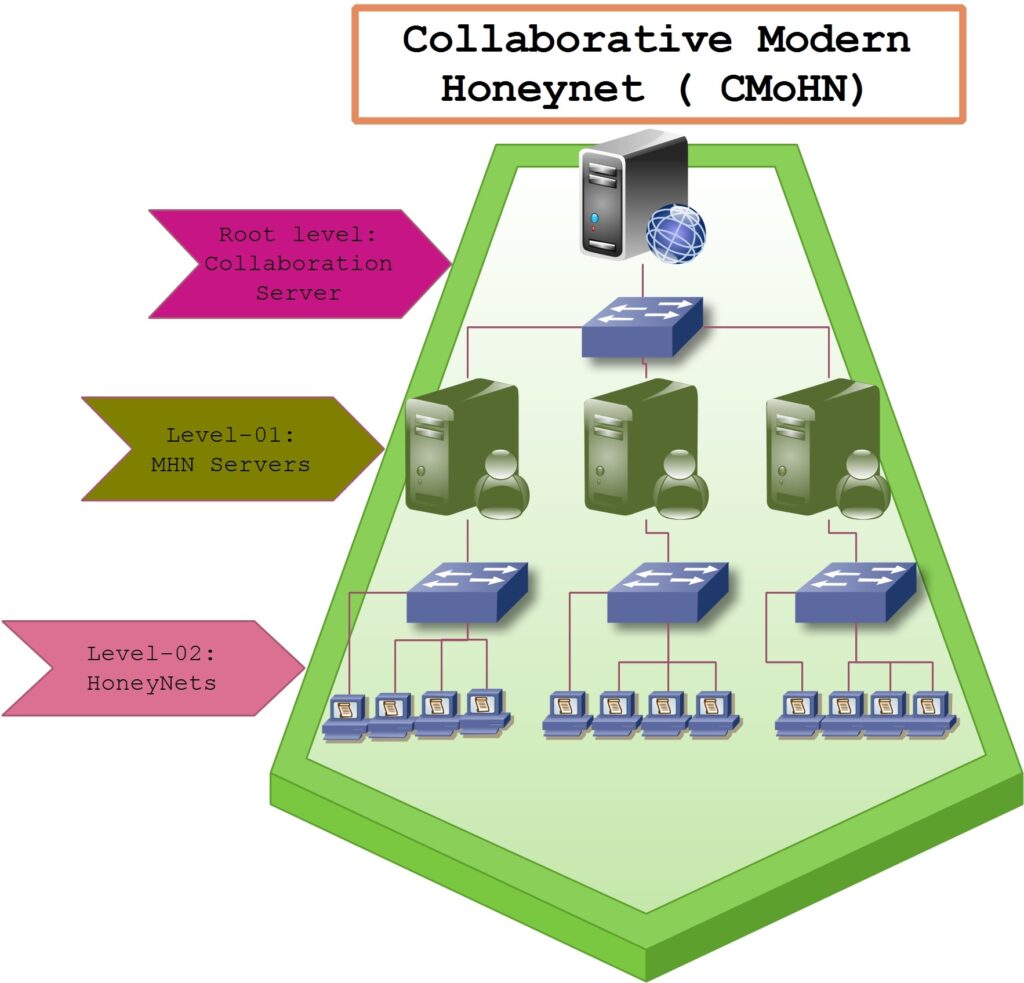
Figure-01: Abstract view of the hierarchy of the Collaborative Modern Honeynet (CMoHN)
Partnership and the Involvement of the Beneficiaries:
Last three objectives of the project involve the activities regarding our partnership and outreach to the potential users or beneficiaries of the project. We have been in close dialogue with a number of organizations to motivate them to deploy the CMoHN system in their organization network thus helping to form the regional collaborative honeynet. We shared our experience with the deployment of the modern honeypots and honeynet in a couple of conferences. We got a very positive response that later on helped some organizations to deploy the honeynet in their organizations. At the moment, we have two types of deployments of honeynets in our region. One is in the collaborative mode and second is in the standalone mode. The collaborative mode deployment is depicted in figure 02 below. RISE campus (Riphah Institute of Systems Engineering at Sector F-5/1, Islamabad) deployment shows the deployment of MHN (Modern Honeynet) in internal (LAN) as well as in external (WAN interface) mode. The collaborative server is also hosted at the RISE campus. MHN deployed at the main campus shows the deployment at the Faculty of Computing, Riphah International University, Sector I-14, Islamabad. A collaborative client is also additionally deployed here. Similarly, the third deployment of MHN is shown at the partner organization place that is located at the Associated Press of Pakistan (APP) office situated at Sector G-7, Islamabad. A collaborative client is additionally deployed at the partner organization place also.
A standalone deployment of MHN has been made at National Engineering and Scientific Commission, Islamabad office. Moreover a couple of deployments of MHN at the Pakistan Atomic Energy Commission, Islamabad and KP IT Board, Cyber Emergency Response Center, Peshawar are under consideration. These organizations belong to the defense department, therefore, they are reluctant to deploy the collaborative client at their locations. That’s why we term their deployment as the standalone deployments.
Table 1: Deployment/Partners table.
| S. No. | Deployment Mode | Organization | Status |
| 1 | Collaborative | Riphah Institute of Systems Engineering (RISE) | Completed |
| 2 | Collaborative | Faculty of Computing, Riphah International University | Completed |
| 3 | Collaborative | Associated Press of Pakistan (APP) | Completed |
| 4 | Standalone | National Engineering and Scientific Commission | Completed |
| 5 | Standalone | Pakistan Atomic Energy Commission | In Progress |
| 6 | Standalone | KP IT Board, Cyber Emergency Response Center | In Progress |
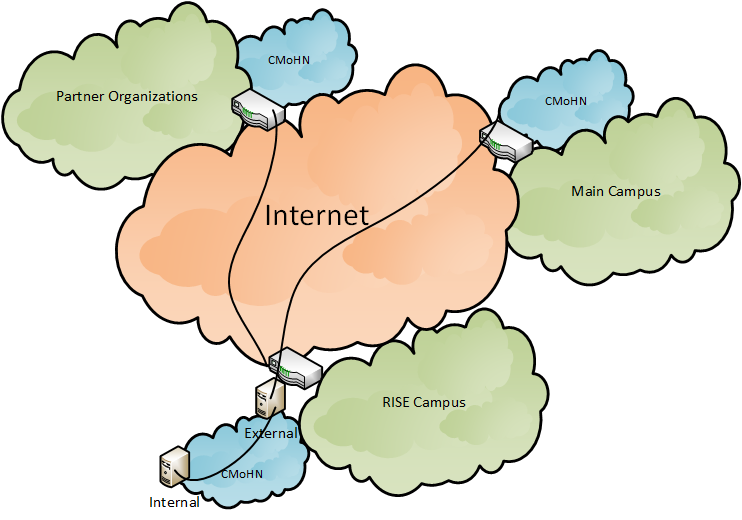
Figure-02: Deployment topology of the Collaborative Modern Honeynet (CMoHN) Project
The project has a small team comprising of a team lead and two research engineers, therefore, the project administration has not been the issue. However, as this is a small grant project having small honorarium for the team members, therefore, it has been difficult to engage the team members on the full-time basis. Although, team members have been very cooperative, however, as team members have also been engaged in their other activities so, this made the management of different activities a little bit challenging.
Due to the financial audit requirements of the university, the project funding is moderated by the university’s finance department. Moreover, we are also bounded to purchase the project equipment through the university’s central procurement department. Also, the university can only deal with its authorized vendors only. This all led to a bit delay in the procurement process of the hardware required for the development and deployment of the project.
This is our first international funded project. The work and progress on this project have inspired the team members and other colleagues at the university to initiate such type of project activities. One of my colleagues recently got an approval of another cybersecurity grant and some other our faculty members are showing their enthusiasm for taking this type of initiatives. This is a cultural change in our organization that is transforming traditional university teachers into the technology practitioners which is very encouraging for us.
Project Evaluation
Considering the increasing number of cybersecurity attacks, CMoHN project is of great importance. There are many dimensions in which this project is contributing. Using this project, organizations would be able to assess the extent to which they are targeted by the cybercriminals on the daily basis. They would also be able to see the attacks on their collaborative partners. This would help them to assess the overall regional cybersecurity landscape. These have been the main objectives of the project and we have largely achieved these objectives. Although, the collaborative module is still in the improvement cycle and we are working to make it more stable in the near future.
Although the project got delayed due to some unavoidable circumstances e.g. unnecessary delays in the university's procurement process and then a further delay in the supply of the server machines from the vendor. But thanks to the isif.asia for extending the project timeline. This indeed helped us to complete our deployments and achieve the project objectives.
There have been many side benefits of this project also. We are a cybersecurity research group and this project has helped us in many ways. We have been able to build our dedicated infrastructure to analyze the cyber attacks. We have a trained workforce in the form of project team members as well as research students that are working on a high-tech real-time cybersecurity project. It has inspired research students to identify the limitations of the current honeynet products and motivated them to work to improve them. These improvements are going on in two directions. One is to develop new honeypots to counter the new attacks and the other is to integrate honeynets with other infrastructure security devices such as firewalls.
| Indicators | Baseline | Project activities related to indicator | Outputs and outcomes | Status |
|---|---|---|---|---|
| How do you measure project progress, linked to the your objectives and the information reported on the Implementation and Dissemination sections of this report. | Refers to the initial situation when the projects haven’t started yet, and the results and effects are not visible over the beneficiary population. | Refer to how the project has been advancing in achieving the indicator at the moment the report is presented. Please include dates. | We understand change is part of implementing a project. It is very important to document the decision making process behind changes that affect project implementation in relation with the proposal that was originally approved. | Indicate the dates when the activity was started. Is the activity ongoing or has been completed? If it has been completed add the completion dates. |
| Internal Deployment of Honeypots and HoneyNet | Neither we had any visibility of cyber-security attacks in our region nor we had any experience of deploying honeypots and honeynets to observe the cyber attack attempts | We formed a project team, purchased the Dell R710 server machine, laptops for the development team, and a switch to connect these devices. Then we created a virtual environment using ESXi on the server machine and deployed honeypots on it on Ubuntu machines and started observing their results. | We had an experimental local deployment of two subnets in the virtual environment with honeynet server in one subnet and the following honeypots in the other subnet: Cowrie, Dionaea, Elastichoney, Glastopf, P0f, Shockpot, Snort, Surricata, and Wordpot. | Completed: Started from 01-09-2016 and completed on 31-12-2016 |
| External Deployment of Honeypots | We had experience of deploying honepots and honeynet but still no visibility of cyber attacks on the public Internet | We purchased a pool of eight public IP addresses and another Dell R710 server machine and started deploying a production honeynet on the public Internet | Soon, we started receiving cyber attack attempts on our public honeynet. Majority of the attacks were observed on the Cowrie, Dionaea and Surricata. | Completed: Started from 01-01-2017 and completed on 30-06-2017 |
| Remote Deployment and Experience Sharing with the Community | We had visibility of cyber attacks on our network. Then, we wanted to deploy the honeynet at remote location and correlate the results of two public deployments. Still local community does not have any idea about the cybersecurity situation in the region. | We prepared a remote location for the deployment, purchased another pool of eight public IP addresses, a Dell R710 server machine with some accessories. We also delivered two public seminars in two research conferences to disseminate our results. | Now, we have two public deployments of honeypots. We observe on average more than 6000 cyber attack attempts on each of these honeypots. After our public seminars, we received a warm reception and started receiving requests for deploying more honeynets. | Completed: Started from 01-07-2017 and completed on 20-04-2018 |
Gender Equality and Inclusion
Encouraging and engaging women in STEM careers in general and cybersecurity, in particular, has been an area of concern for us. We have seen the very low involvement of women (roughly around 10%) in this area. Dr. Yousaf recently included two female faculty members in the department and encouraging them to participate in these projects. Also, motivated one female research student to work on the project. Although, she worked with the project team for a couple of months, however, she could not complete her work and then changed her research area. At the moment, we are motivating more female students to work on this type of cybersecurity projects.
Project Communication Strategy
In order to share the experience of this project and to benefit the intended audience, we had a plan with three different dimensions. One is to arrange a couple of awareness seminars, second is to publish the design and result in reputed conferences/journals, and third is to partner with the different organization who can deploy our system in their networks. Luckily, we got the opportunity to share our experiences of this funded project in a couple of reputed IEEE conferences as a guest speaker. This opportunity server our first two objectives of the communication and dissemination. The first conference was the IEEE 15th International Conference on Frontiers of Information Technology (FIT 2017) held from December 18, 2017 to December 20, 2017 in Islamabad, Pakistan. The second conference was the IEEE 15th International Bhurban Conference on Applied Sciences and Technology (IBCAST 2018) held from January 08, 2018 to January 12, 2018 in Islamabad, Pakistan.
These conference speeches helped us to not only share our experience of this funded project but also provided us the opportunity to spread awareness about the isif.asia funding opportunities and the role of isif.asia to promote research and development culture and community development projects. This also helped us to provide facilitation partnership to couple defense organizations to set up honeypot and honeynet deployments in their own organizations. We not only share our experience but also we shared our collected data of the experience cyber security attacks with these organizations.
Table 2: Seminar/Talks.
| S. No. | Title of Talk | Conference Name | Organizer | Date | Location |
| 1 | Experiences of Modern Honeypots and Honeynet (Knowing our cybersecurity landscape) | IEEE 15th International Conference on Frontiers of Information Technology (FIT 2017) | Comsats University, Islamabad | December 18, 2017 | Serena Hotel, Islamabad |
| 2 | Experiences of Modern Honeypots and Honeynet (Knowing our cybersecurity landscape) | IEEE 15th International Bhurban Conference on Applied Sciences and Technology (IBCAST 2018) | Center of Excellence in Science and Applied Technologies (CESAT), Islamabad | January 11, 2018 | National Center of Physics, Quaid-e-Azam University, Islamabad |
Recommendations and Use of Findings
Honeypots and honeynets have mostly been deployed in the test setups only. At least in our region (Pakistan), we have not seen any deployment of honeypots and honeynets in the production networks. The result of this lack of deployment is the low visibility of the extent of the cyber-attacks. The practitioners in our region have to rely on the cybersecurity reports published from the other countries in order to remain ready to counter the cyber-attacks. There is a need to make industry people aware of the benefits of deploying the honeypots and honeynets. This would give them the early detection of the cyber-attacks and could save them from the potential damages. Moreover, there is also a need to do more R&D work in creating new honeypots especially the ones for detecting the cyber-attacks exploiting the IoT devices and ones that could detect the ransomware attacks. Both of these types of attacks are rising and there is a dire need to do more work to counter these types of attacks.
We are thankful to the ISIF Asia Internet Society Cybersecurity Grant for funding this project. It has provided us a platform where we can motivate research students to develop new honeypots and with the successful experience of the project, we are in a better position to motivate other industries to deploy these technologies to improve the overall cyber-health of the Internet.
Bibliography
Danyliw, R. (2016). RFC 7970: The Incident Object Description Exchange Format Version 2. IETF.
Kadobayashi, Y., & al., e. (2014). RFC 7203: An Incident Object Description Exchange Format (IODEF) Extension for Structured Cybersecurity Information. IETF.
Mokube, Iyatiti, & Adams, M. (2007). Honeypots: concepts, approaches, and challenges. 45th annual southeast regional conference (pp. 321-326). ACM.
Montville, A., & Black, D. (2015). RFC 7495: Enumeration Reference Format for the Incident Object Description Exchange Format (IODEF). IETF.
Moriarty, K. (2010). RFC 6545: real-time inter-network defense (RID). Internet Engineering Task Force (IETF).
Spitzner, & Lance. (2003). Honeypots: Catching the insider threat. 19th Annual Computer Security Applications Conference, 2003 (pp. 170-179). IEEE.
Spitzner, & Lance. (2003). The honeynet project: Trapping the hackers. IEEE Security & Privacy, 99(2), 15-23.
Trammell, B. (2012). RFC 6546: Transport of Real-time Inter-network Defense (RID) Messages over HTTP/TLS. IETF.
Trammell, B. (2012). RFC 6684: Guidelines and Template for Defining Extensions to the Incident Object Description Exchange Format (IODEF). IETF.
Trammell, B. (2012). RFC 6685: Expert Review for Incident Object Description Exchange Format (IODEF) Extensions in IANA XML Registry. IETF.
Zhang, Feng, Zhou, S., Qin, Z., & Liu, J. (2003). Honeypot: a supplemented active defense system for network security. Fourth International Conference on Parallel and Distributed Computing, Applications and Technologies, 2003. PDCAT'2003 (pp. 231-235). IEEE.
This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 


