TECHNICAL REPORT
| Grantee |
Prof Vijay Varadharajan and Dr Uday Tupakula
|
| Project Title | Software Defined Networks based Security Architecture for IoT Infrastructures |
| Amount Awarded | USD 21,600 |
| Dates covered by this report: | 2018-02-01 to 2019-05-31 |
| Report submission date | 2019-05-31 |
| Economies where project was implemented | Australia |
| Project leader name |
Prof Vijay Varadharajan
|
| Project Team |
Dr Uday Tupakula
[email protected]
Kallol Krishna Karmakar
[email protected]
|
| Partner organization | N/A |
Project Summary
There has been a rapid growth in the Internet of Things (IoT), with an ever-increasing number of physical devices being connected to the Internet at an unprecedented rate; recent forecasts suggest the number of IoT devices will reach 31 billion in 2020 [8]. These IoT devices are heterogeneous with different operating systems and connectivity capabilities ranging from wireless to mobile networks, often deployed in somewhat uncontrolled and untrustworthy environments, can pose significant and somewhat unique challenges in security and privacy. The main goal of the proposed project was to develop a secure IoT architecture by leveraging the underlying features supported by Software Defined Networks (SDN). The project developed fine granular security policies and a lightweight security protocol to authenticate IoT devices and authorise them to access services in network infrastructure in a secure manner. The project involved three stages. In the first stage, we conducted a detailed study of security attacks on IoT infrastructures and the different security solutions that currently exist to counteract the various types of attacks. Then we analysed the pros and cons of the existing solutions, and developed security requirements that need to be addressed in designing security architecture for IoT Applications. As part of second stage, we developed a lightweight authentication protocol based on a novel public key encryption scheme. The proposed protocol achieved a balance between the efficiency and communication cost without sacrificing security. In the third stage, we proposed a SDN based security architecture for IoT systems. Our security architecture allowed specification of fine granular access policy constraints on communications between end users, devices and services in a distributed environment. A novel feature of the proposed architecture is its ability to specify path based security policies, which is a distinct advantage in SDNs.
Table of contents
- Project factsheet information
- Background and justification
- Project Implementation
- Project Evaluation
- Gender Equality and Inclusion
- Project Communication Strategy
- Recommendations and Use of Findings
- Bibliography
Background and Justification
Although IoT has huge potential, it comes with a number of key security challenges—IoT devices can become the entry points into smart homes and organisation networks including critical infrastructures. IoT devices are small, have limited energy source and capabilities, and less powerful with respect to processing of information. Hence an attacker is able to easily target these things, by sending fake requests, intercepting/ manipulating valuable sensor data in transit or capturing a physical device and transforming it to zombies to launch attacks. Furthermore often it is not possible to enhance security of these devices using traditional defence mechanisms as they are located in open premises and they incur extra processing load to small IoT devices. However, if proper security mechanisms are not provided, then there is risk of information leakage, illegal data modification and large scale denial of service attacks. Illegal tampering of data can also lead to wrong decisions made using this data by users and other services which are highly significant and will have a significant impact on the payoff for enterprises deriving value from IoT data analytics. Data driven decision-making capabilities creating enhancing productivity enabling new market opportunities critically depend on the trustworthiness of the data from the IoT devices. The proposed project is aimed at developing a network based solution that can secure the IoT device network infrastructure enabling secure decision making applications.
Our approach to developing a secure the IoT based network infrastructure is based on the following: First, the idea behind our solution is that only authenticated data and devices can see the underlying network services. So an important question in our work is how to authenticate the data from IoT devices so that only authenticated data can be consumed by other services and stored in the cloud. Then we will leverage Software Defined Networks to achieve the security of the IoT network architecture. The objective behind this is that this will enable us to develop security policies that are fine granular and specific to IoT devices, services and network entities, thereby ensuring to control and secure the infrastructure. Furthermore, it will make use of the domain wide visibility to achieve effective security management. We will ensure integrity of IoT data using a lightweight elliptic curve based cryptographic protocol, and enable secure delegated access for IoT devices using an integrated OAuth based SDN architecture. Hence our work is aimed at the development of IoT security architecture that can achieve secure policy driven decision making with trustworthy data while helping to cope with defend against security attacks.
Hence the contributions from our project include the following:
- A SDN based security architecture for IoT infrastructure
- Security services for authentication of IoT devices and data integrity using SDN
- Access control policies for achieving secure interaction between IoT devices and enabling secure policy driven decision making with IoT data
- Practical example scenario for defending IoT devices against security attacks such as Mirai botnet DDoS attacks against the IoT infrastructure
Some Recent Related Works
There have been some recent works that have used SDN to control the IoT infrastructure. The work by Chakrabarty et al. [1] is concerned with secure IoT communications and encrypts both header and payload of the packets, and use the SDN Controller as a trusted third party. This is helpful for preventing traffic analysis attacks but adds computational complexity and reduces bandwidth. Sandor et al. [2] try to improve the resilience of IoT communication by using SDN's routing feature. They assume that there are several redundant routers for the communication in IoT networks. When one communication link is disabled by attacks, they use the SDN controller to select a new link for the communication. Bull et al. [3] propose a method to detect and mitigate anomalous behaviour at the SDN-based IoT gateway by pre-setting flow entries and gathering source and destination statistics of flows and classifying the network state. In [4], SDN is used in the IoT infrastructure for managing the large amount of data that is being generated and for maintaining the QoS of the network. In [5], a preliminary study of building and managing cluster networks using SDN has been investigated.
Some other related works include the techniques for profiling of the devices to generate fingerprints and making use of techniques such as crowd sourcing, whitelists and blacklist to assess the risk potential [6,7]. However, such piece meal solutions with static level restrictions are not effective against the attacks in practice. Our approach leads to a comprehensive security architecture addressing relevant aspects such as how to identify and authenticate devices in networks consisting of several heterogeneous devices with cross device dependencies; how to achieve end-to-end secure communication between the devices; how to secure the communication of tiny IoT devices which cannot perform any encryption; how to monitor the behaviour of the heterogeneous devices in real time and isolate malicious devices.
Organizational Context
This project is carried out within the Advanced Cyber Security Engineering Research Centre (ACSRC) at the University of Newcastle’s Faculty of Engineering. The ACSRC has access to labs and infrastructure for the demonstration of the project’s results.
The overall aim of the Advanced Cyber Security Engineering Research Centre (ACSRC) is to achieve fundamental advances in the theory, design and management of models and techniques that will enable secure and dependable computing information systems and services.
An important characteristic of ACSRC is its research capabilities and expertise covering both theory and practice in addressing the challenges that arise in achieving secure systems in a heterogeneous mobile distributed environment involving distributed systems, wireless, broadband and peer to peer networks, mobile devices and distributed information services.
Currently we have research projects in the areas of Cloud Security, Secure Virtualization, Internet of Things (IoT) Security, Big Data Security, Trusted Computing, Software Defined Networks Security, Malware and Security Attacks, Data Analytics for Malware Analysis, Secure Systems Design, Peer to Peer Applications, Formal Security Techniques and Applied Cryptography.
A key feature of security research is its multi-faceted nature with security acting as a thread that sews multiple technologies, applications, models and polices together.
It is increasingly evident that challenges do not come in self-contained neat packages (be they in healthcare or intelligent transportation or finance or ecommerce) and it is critical for research in technology and policy should go hand in hand to deal with complexity and inter-dependability and achieve the desired outcomes.
Project Implementation
Project’s Objectives
The project had the following objectives:
- Conduct a study of security threats and attacks in IoT infrastructures and the types of techniques and mechanisms that can be used to counteract them
- Develop an efficient authentication protocol and mechanism for small IoT devices with limited computational capabilities. In particular, in this project, we will investigate the design of an identity based key establishment protocol using elliptic curve cryptography for authentication of IoT devices and OAuth (Open Authorisation) for associating credentials with authenticated IoT devices.
- Develop a network-based architecture solution that can secure the IoT device network infrastructure leveraging software defined network (SDN) technologies. In particular, our objective is to design a policy driven SDN architecture for securing IoT infrastructures, specifying security policies which can be enforced on distributed IoT devices and dynamically route the IoT traffic to their appropriate network entities and end services in a secure manner.
- Apply the developed security architecture, security protocol and mechanisms to a practical example scenario to protect IoT devices and infrastructures from various types of DDoS attacks such as Mirai.
Project Implementation
Stage 1
The project started with Stage 1 by conducting a detailed investigation of security threats and attacks in IoT infrastructures and the types of techniques and mechanisms that can be used to counteract them. The Stage 1’s work has been described in a detailed Technical Report TR1 on “Study of Security Attacks against IoT Infrastructures”. May 2018, 32 pages. See the Advanced Cyber Security Research Center technical reports section for more.
In Stage 1 Report, we started with an overview of the IoT architecture with its different layers and protocols that are used in these layers. Then we considered a threat model for the IoT Architecture with a discussion on the several attacks that are possible at different layers of the IoT Architecture. We also proposed the design and development of feature distributed malware attacks for ternet of Things in the context of smart homes. Smart homes consist of various smart home devices, providing convenient services to the tenants. These devices are usually connected to the ternet, and the tenants can integrate individual devices and make smart home workflows using ternet services such as IFTTT (If This Then That). The focus of our work was on how the attackers can generate various cyber-physical and advanced cyber-attacks by exploiting this integration aspect in smart home. particular, we have designed and developed an advanced feature distributed malware that can be used to perform various malicious activities such as stealing the victim’s IFTTT cookies, using smart devices as information sources of the malware and distributing malware functionalities to other devices, performing malicious without being noticed, causing financial damages to the victim, and evasively exfiltrating data. Our experiments showed that the proposed attacks enable the attackers to control any smart home device integrated with IFTTT, without requiring compromise of individual smart home devices. We believed our approach of using the integrating ternet service as an attack vector and distributing malware features to the smart home devices will be helpful to the development of more secure smart home environments and different IoT applications. Finally, we analysed some of the previously proposed techniques to deal with the attacks in IoT applications and identified few security requirements that need to be considered for designing and for developing security architecture for IoT applications.
IoT architecture consists of four basic layers: Perception Layer, Network Layer, Middleware Layer, and Application Layer [9] . Table 1 shows the components of each layer and their tasks in details.
Table 1 - IoT layer details
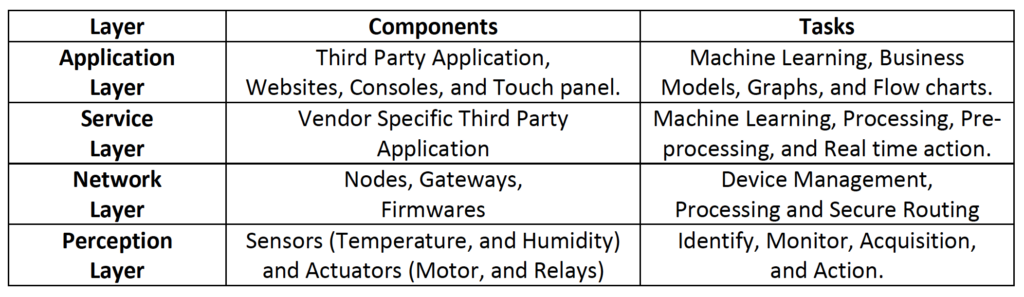
Table 2 - Protocols used in different layers
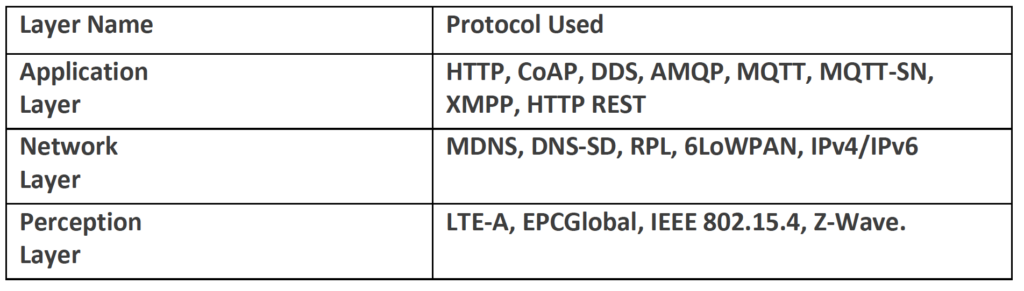
Figure 1 - Attacks in different layers of the IoT Architecture
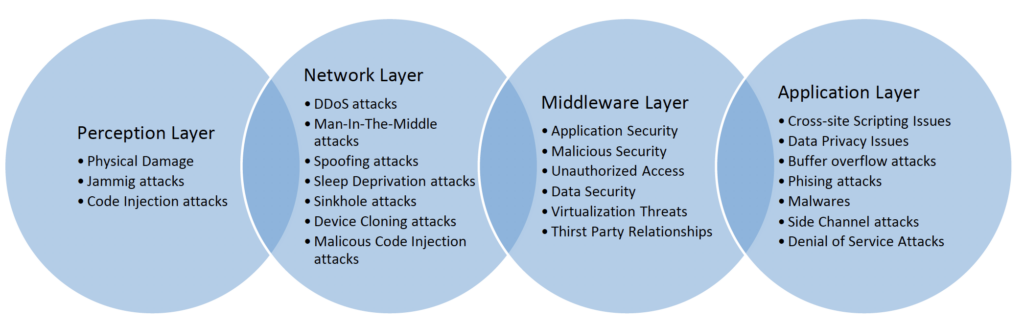
Figure 2 - IFTTT recipe examples for smart home
Since the emergence of smart home devices, IFTTT started supporting such devices so that its users can automate a wide range of smart home tasks such as maintaining a certain temperature using smart thermostats and an air conditioner as illustrated in Figure 2.
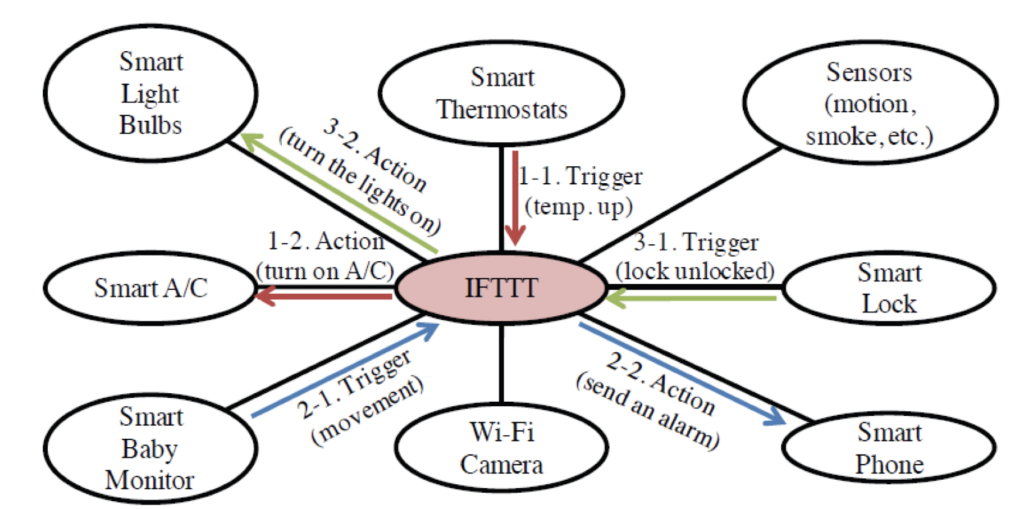
Figure 3 - Target smart home configuration
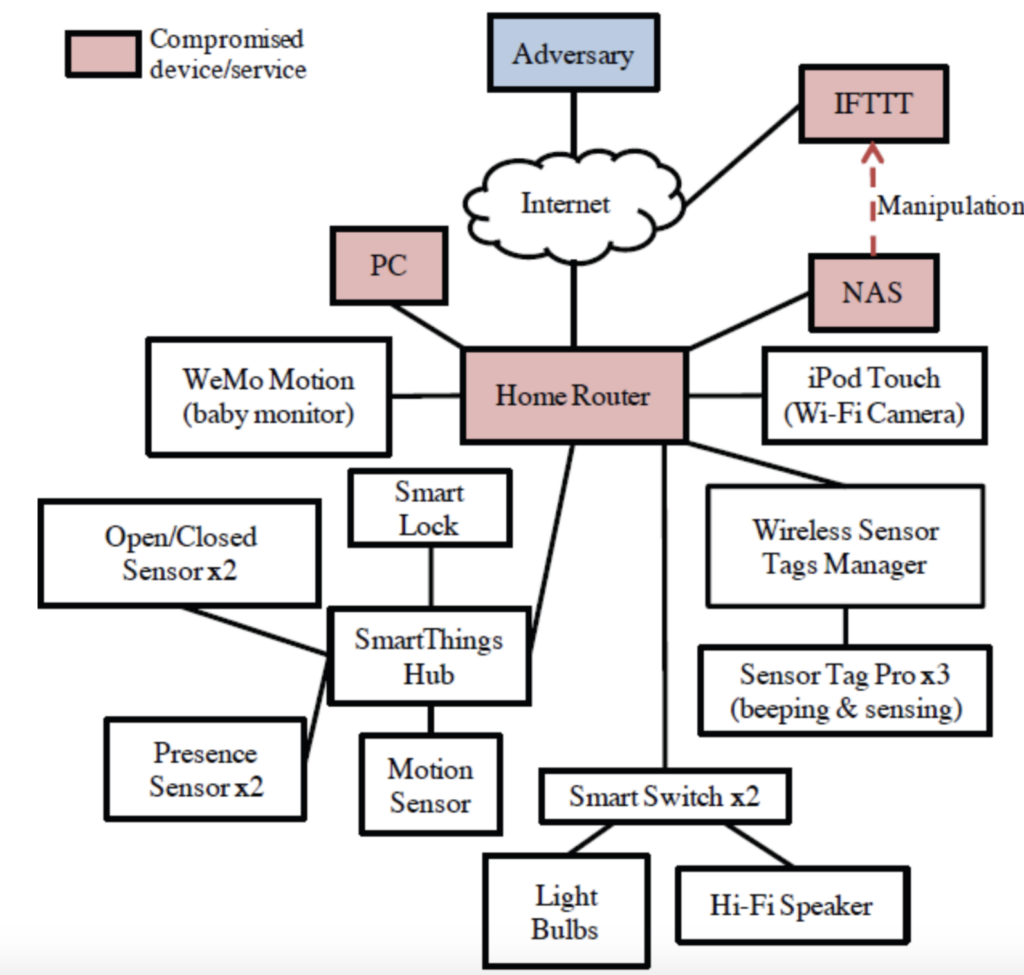
The configuration of our target smart home consists of a smart lock, a baby monitor, a Wi-Fi camera (iPod Touch), smart sensors (temperature, motion, and/or humidity), beeping tags, smart switches, sensor & tag mangers, a home router and a NAS, as illustrated in Figure 3.
Stage 2
Stage 2 of the project addressed two aspects: i) Design of the Lightweight Authentication Protocol for IoT and ii) Security Analysis of the Authentication Protocol for IoT. The Stage 2’s work has been described in a detailed Technical Report TR2 on “Lightweight Authentication Mechanism and OAuth Protocol for IoT Devices”, Oct 2018, 25 pages. See the Advanced Cyber Security Research Center technical reports section for more.
First we developed a lightweight mutual authentication protocol based on a novel public key encryption scheme for smart city applications. The proposed protocol takes a balance between the efficiency and communication cost without sacrificing the security. We evaluated the performance of our protocol in software and hardware environments. For a given security level, our protocol performance is significantly better than existing RSA and ECC based protocols. We also provided security analysis of the proposed encryption scheme and the mutual authentication protocol. The proposed protocol is an n-pass lightweight mutual authentication protocol. The value of n is related to the desired security level of the protocol and the system parameters of the encryption scheme. Our lightweight mutual authentication protocol applies the proposed encryption scheme as a building block. The security of the proposed n-pass mutual authentication is guaranteed by the security of the Needham-Schroeder protocol. We show that our protocol can resists attacks such as man-in-the-middle attack and impersonation attack. We evaluated the protocol on Contiki OS and CC2538 evaluation modules. The experimental evaluations show that our protocol is respectively 88 and 7 times faster than RSA and ECC on the security level of 112 bits. The mutual authentication time can be further reduced if online/offline technique is enabled.
Figure 4 - Smart City Applications
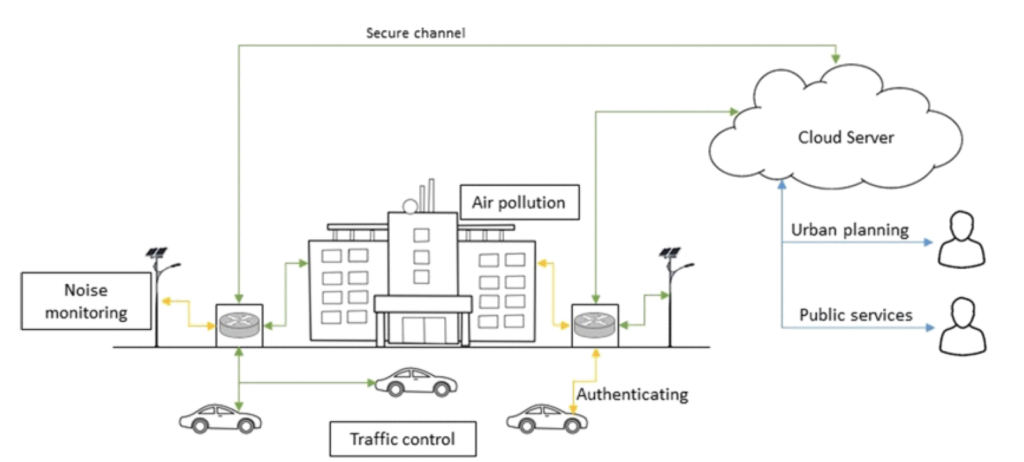
IoT enabled Smart City applications are based on diverse type of devices and technologies. Figure 4 shows an example of Smart Citiy scenario where the system observes environmental information, such as air quality, noise level and traffic congestion, for urban planning and public services.
Figure 5 - Device-to-device mutual authentication using CC2538 evaluation modules

Figure 5 shows the evaluation modules we used CC2538 to test the performance of our protocols.
Stage 3
Stage 3 of the project addressed the development of the security architecture for IoT and it consisted of the following tasks: i) Design of Security Architecture and Attack Detection in IoT Infrastructures and ii) Proof of Concept of Security Architecture for IoT. The Stage 3’s work has been described in a detailed Technical Report TR3 on “Security Architecture for IoT”, April 2019, 34 pages. See the Advanced Cyber Security Research Center technical reports section for more.
nderlying features supported by Software Defined Networks (SDN). Our security architecture restricts network access to authenticated IoT devices. We use fine granular policies to secure the flows in the IoT network infrastructure and provide a lightweight protocol to authenticate IoT devices. The security policies are based on parameters such as user, device, switch/gateway, location, routing information, services accessed as well as trust labels associated with the switches and controllers in different domains. We have also considered on demand security of user data by encrypting the traffic at the edge device and decrypting the traffic at a device closer to the destination (which is intended to receive the traffic). A novel feature of the proposed architecture is its ability to specify path based security policies, which is a distinct advantage in SDN enabled IoT infrastructures. For instance, certain IoT communications need to go through a path of switches with certain security attributes. Such path based policies are critical for secure applications but also useful for normal applications with different requirements (e.g. bandwidth requirements for different traffic such as audio versus video traffic. At another level, our policies is able to specific rules reflecting social aspects such as devices belonging to certain groups of users such as ethnicity or gender as well as constraints related to certain cultures such as different cultural organizations and their attributes. Such features can address various characteristics associated with social norms and ethics associated with the data collected from these devices as well as expected interactions between various devices in different domains. These can be achieved due to fine granular nature of the policies and its ability to reflect the context and their associated characteristics.
An overall feature of the security architecture is its ability to make use of the dynamic visibility of the network connectivity and the flows in the network in achieving dynamic updates to security policies for achieving secure communications. This is particularly important with emerging new security threats and the need to dynamically update security policies based on the distributed network state and detection of new anomaly events. Such an integrated security approach involving authentication of IoT devices and enabling authorized flows can help to protect IoT networks from malicious IoT devices and attacks such as IoT botnet based DDoS attacks. We have implemented and validated our architecture using ONOS SDN Controller and Raspbian Virtual Machines, and demonstrated how the proposed security mechanisms can counteract malware packet injection, DDoS attacks using Mirai, spoofing/masquerading and Man-in-The-Middle attacks.
Figure 6 - Security Architecture for IoT Network Infrastructure
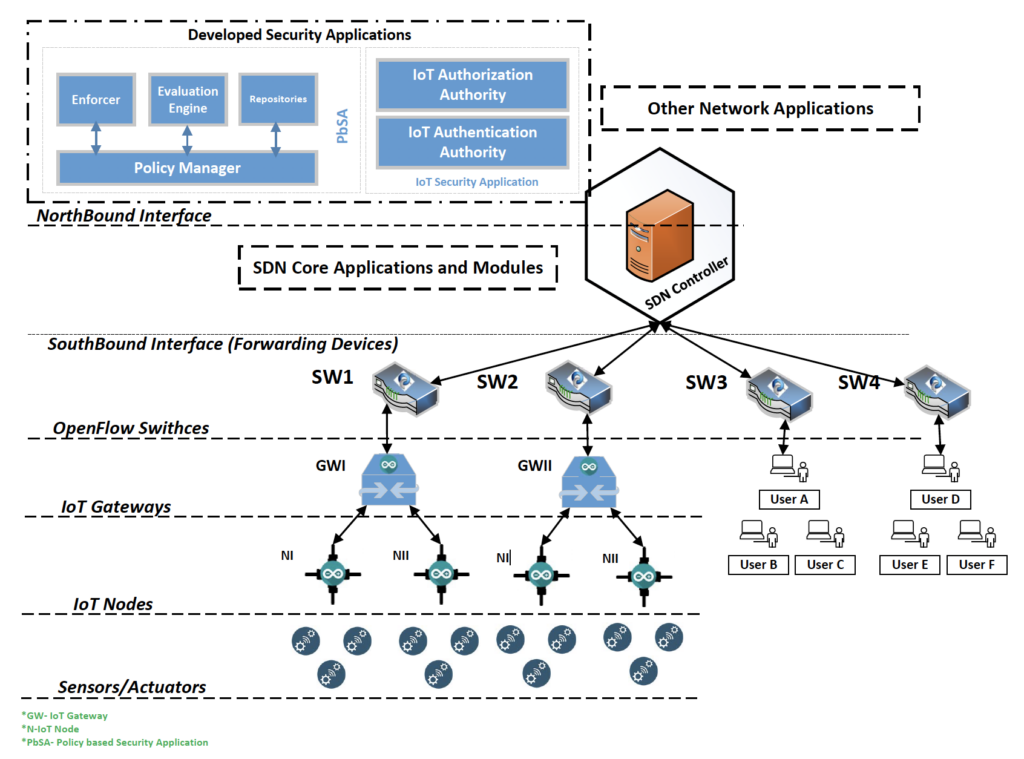
Figure 6 shows the proposed SDN based security architecture. The heart of the security architecture is the SDN Controller where security policies reside and are evaluated. The IoT actuators and sensors are the end devices and connect to the IoT Nodes. These IoT Nodes are connected to the IoT Gateways via either via wired or wireless networks. The IoT Gateways are connected to the SDN Controller.
Figure 7 - Security Protocol process diagram
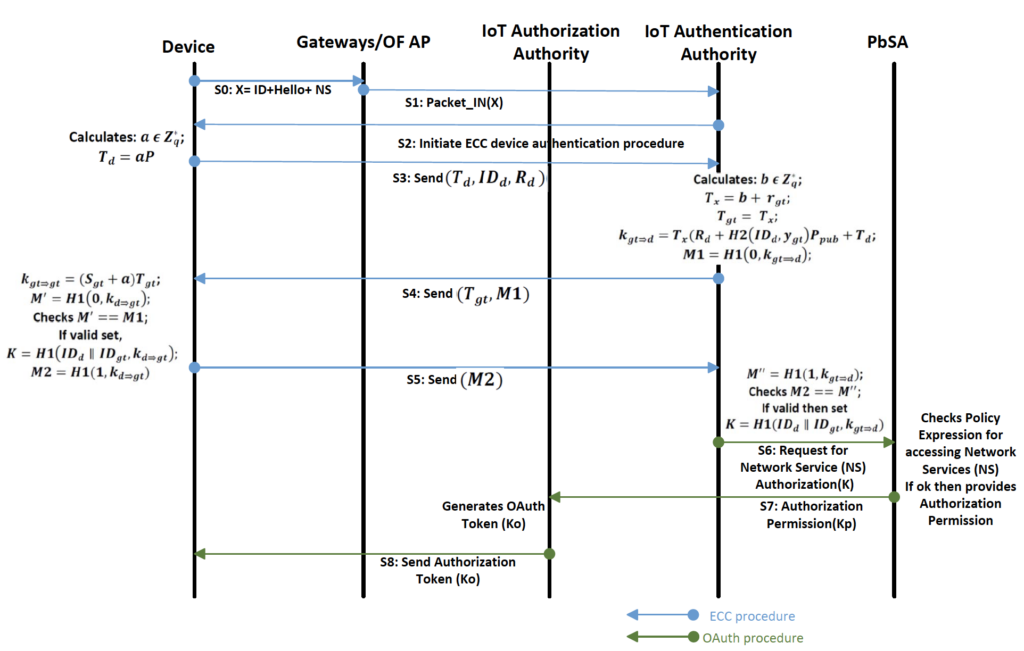
The security protocols used in our security architecture are implemented by the IoT Security Application (ISA). Figure 7 illustrates the security protocol process in the authorization phase of the IoT Authentication Authority.
Figure 8 - Implemented Network with Routing Information
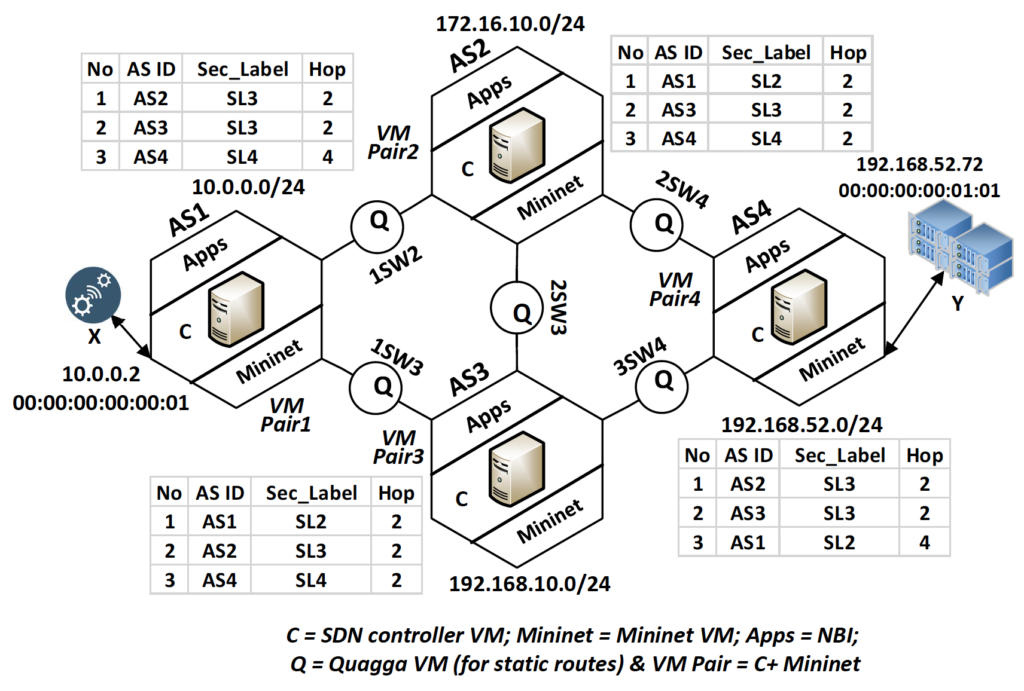
We used the inter-domain scenario given in Figure 8 to illustrate the various steps involved in Security Architecture Walk-through. The Tables beside each of the AS domains in Figure 8 represent the Topology Repository.
Figure 9 - Network configuration
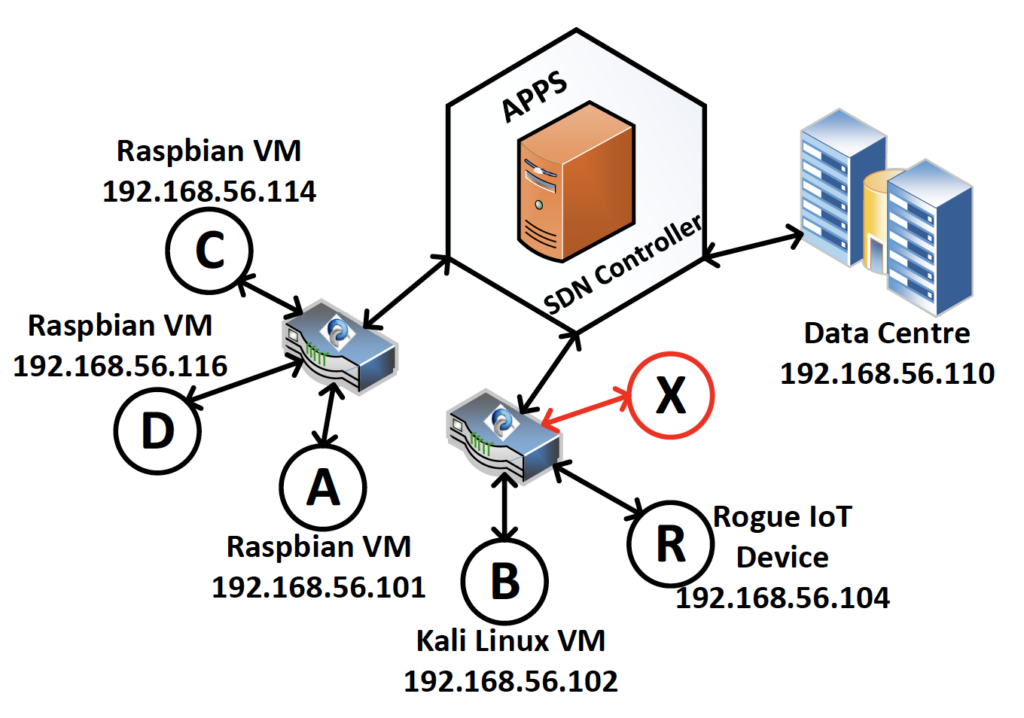
Project Evaluation
Achieved Objectives
- In terms of the project’s objectives, all the objectives 1 to 4 have been achieved.
Important Findings of the Project
- Stage 1 produced a detailed investigation of security threats and attacks in IoT infrastructures and the types of techniques and mechanisms that can be used to counteract them. The Stage 1’s work has been described in a detailed Technical Report TR1 on “Study of Security Attacks against IoT Infrastructures”, May 2018, 32 pages. See the Advanced Cyber Security Research Center technical reports section for more.
- Stage 2 resulted in: i) Design of the Lightweight Authentication Protocol for IoT and ii) Security Analysis of the Authentication Protocol for IoT. The Stage 2’s work has been described in a detailed Technical Report TR2 on “Lightweight Authentication Mechanism and OAuth Protocol for IoT Devices”, Oct 2018, 25 pages. See the Advanced Cyber Security Research Center technical reports section for more.
- Stage 3 resulted in (i) Design of the security architecture for IoT and ii) Proof of Concept of Security Architecture for IoT. The Stage 3’s work has been described in a detailed Technical Report TR3 on “Security Architecture for IoT”, April 2019, 34 pages. See the Advanced Cyber Security Research Center technical reports section for more.
Benefits
- The developed prototype has been used to demonstrate how certain attacks can be counteracted in the IoT infrastructure. The outcomes have made a positive impact in terms of protecting IoT infrastructures against specific attacks. This has been shown with system prototype. See Our Publication [1] below.
Further Development planned after the ISIF Asia grant has been completed:
- We are currently planning to develop a demo of our prototype in the form of a video which can be shown using a laptop in various industry forums and events
- We also envisage to enhance the security architecture and the prototype to incorporate additional policies and mechanisms to counteract further attacks in the future
Capacity building
- This project has resulted in building of capacity at our institution (the University of Newcastle) in terms of security expertise in SDN and IoT as well as development of a specific individual (PhD student - Kallol Krishna Karmakar), who has now completed his PhD (which included some of the work done in this project). The student's name appears in all the Technical Reports. See the Advanced Cyber Security Research Center technical reports section for more.
| Indicators | Baseline | Project activities related to indicator | Outputs and outcomes | Status |
|---|---|---|---|---|
| How do you measure project progress, linked to the your objectives and the information reported on the Implementation and Dissemination sections of this report. | Refers to the initial situation when the projects haven’t started yet, and the results and effects are not visible over the beneficiary population. | Refer to how the project has been advancing in achieving the indicator at the moment the report is presented. Please include dates. | We understand change is part of implementing a project. It is very important to document the decision making process behind changes that affect project implementation in relation with the proposal that was originally approved. | Indicate the dates when the activity was started. Is the activity ongoing or has been completed? If it has been completed add the completion dates. |
| Improved mechanisms for counteracting security attacks in IoT infrastructures | Lack of security functionality in IoT infrastructures | See Tasks in the 3 Stages in Reports of Stages 1, 2 and 3. See (https://www.newcastle.edu.au/research-and-innovation/centre/advanced-cyber-security-research-centre/technical reports). | See Reports of Stages 1, 2 and 3 for the outcomes related to Tasks in each Stage. See (https://www.newcastle.edu.au/research-and-innovation/centre/advanced-cyber-security-research-centre/technical reports) | All Stages completed. Stage 1: Feb 2018 - May, 2018, Stage 2: June 2018- Oct 2018, and Stage 3: Nov 2018- April 2019 |
| Achieveable/Appropriate | Lack of integrated security mechanisms for IoT | Develop a system to protect against masquerading, unauthorised access as well as communication attacks in IoT | Design of an integrated security architecture for IoT comprising authentication, access control and secure communications in IoT infrastructures. | Stage 2 (June 2018 till Oct 2018) and Stage 3 (Nov 2018 to April 2019) |
| Relevant | Lack of security architecture counteracting a range of IoT attacks | Demonstrate the applicability of the security architecture to counteract realistic attacks | Proposed secuity architecture demonstrated to counteract practical malware packet injection attacks, Mirai DDoS attacks and spoofing attack using Man-in-The-Middle. | Stage 3: Nov 2018- April 2019 and Presentation of System in International Conference in Washingtom, April 2019 |
Gender Equality and Inclusion
The main motivation for the project was to develop a security architecture for IoT infrastructure that can be used in a range of applications involving IoT devices whether it is in agriculture or healthcare. Such an IoT based infrastructure is increasing being used in the developing economies and hence securing the communications and access in these infrastructures will be increasingly significant, thereby helping to improve inclusion.
Diversity
- In terms of diversity, the project helped to support the work of a PhD student (Kallol Krishna Karmakar) who comes from Bangladesh. We would especially like to acknowledge the support of APNIC in this context.
Project Communication Strategy
As an ISIF Asia Cyber Security Research project, the most direct users of our findings are in the research sphere in Cyber Security as well as the network providers such as the ISPs who are beginning to adopt the SDN and NFV frameworks, and will do more so in the context of 5G in the future.
The following activities were undertaken to inform these users of our work, publically available online. (Also see the publications section of the Advanced Cyber Security Engineering Research Centre)
- K. Karmakar, V. Varadharajan, S. Nepal, U. Tupakula, “SDN Enabled Secure IoT Architecture”, IFIP/IEEE International Symposium on Integrated Network Management, April 2019
- U.Tupakula, V.Varadharajan, K.Karmakar, “Access Control based Dynamic Path Establishment for Securing Flows from the User Devices with different Security Clearance”, 33rd International Conference on Advanced Information Networking and Applications (AINA) March 2019
- K.K. Karmakar, V. Varadharajan, U. Tupakula, "Mitigating Attacks in Software Defined Networks" Journal of Cluster Computing, Jan 2019
- V.Varadharajan, V., K. Karmakar, K., U. Tupakula, “A policy based security architecture for software-defined networks” IEEE Transactions on Information Forensics and Security. 14, 4, p. 897-912 16 p., Apr 2019
- K. Sood, V. Varadharajan, K. Karmakar, U.Tupakula, "Analysis of Policy-based Security Management System in Software-defined Networks", IEEE Commun Letters, accepted Feb 2019
- U.Tupakula, “Design of SDN Security Architecture and its Applications”, SDN Workshop, New Zealand, Feb 2019
- V.Varadharajan, Keynote, “Security Challenges in Software Defined Networks Policy based Security Architecture for Software Defined Networks” , IEEE International Conference ISPA 2017
Recommendations and Use of Findings
Applications and Use of Findings
The developed security architecture can be applied in a range of scenarios such as smart IoT based services in smart cities to smart home applications to healthcare application involving various IoT sensors in a hospital to sensors based applications in agriculture and transport sectors. Our lightweight authentication protocol as well as fine granular access policies make the security architecture suitable for a range of applications mentioned above.
This project has been instrumental in enabling the design and development of this IoT security architecture. Though we have analysed our prototype implementation and showed its performance and security characteristics, it is necessary to take this work further and apply it in a more large scale real world scenarios. As mentioned earlier, this work could be particularly relevant to economies in Asia which are increasingly adopting the use of IoTs in their various business sectors such as transport, agriculture and healthcare. Our recommendation will be to explore this avenue which we believe will be highly beneficial as well as necessary as more and more IoT devices get deployed.
We are very grateful for the ISIF secretariat's flexibility by extending the project to 30 May 2019 thereby enabling us to complete all the work and present our findings at an international conference in April 2019.
Bibliography
References
- S. Chakrabarty, D. W. Engels, and S. Thathapudi, ``Black SDN for the Internet of Things,'' in Proc. IEEE 12th Int. Conf. Mobile Ad Hoc Sensor Syst. (MASS), Dallas, TX, USA, Oct. 2015, pp. 190_198.
- H. Sándor, B. Genge, G. Sebestyén-Pál, ``Resilience in the Internet of Things: The software Defined Networking Approach,'' in Proc. IEEE Int. Conf. Intell. Comput. Commun. Process. (ICCP), Cluj-Napoca, Romania, Sep. 2015, pp. 545_55
- P. Bull et al., ``Flow based security for IoT devices using an SDN gateway,'' in Proc. IEEE 4th Int. Conf. Future Internet Things Cloud (FiCloud),Vienna, Austria, Aug. 2016, pp. 157_16
- Y. Lu, Z. Ling, S. Zhu, and L. Tang, “Sdtcp: Towards datacenter tcp congestion control with SDN for IoT applications,” Sensors, vol. 17, no. 1, p. 109, 2017.
- C.Gonzalez et al., “SDN-Based Security Framework for the IoT in Distributed Grid”, IEEE International Multidisciplinary Conference on Computer and Energy Science, 2016
- M.Miettinen, S. Marchal, I. Hafeez, T. Frassetto, N. Asokan, A. Sadeghi, S. Tarkoma, "IoT Sentinel Demo: Automated Device-Type Identification for Security Enforcement in IoT", IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, June 2017.
- J. Habibi, D. Midi, A. Mudgerikar, E. Bertino, "Heimdall: Mitigating the Internet of Insecure Things", IEEE Internet of Things Journal, Vol. 4, No. 4, August 2017
- Forbes, 2017 IoT Forecasts, https://www.forbes.com/sites/louiscolumbus//2017/12/10/2017-roundup-of-internet-of-things-forecasts/
- L. Da Xu, W. He, and S. Li, "Internet of things in industries: A survey," IEEE Transactions on industrial informatics, vol. 10, no. 4, pp. 2233-2243, 2014.
Our Publications from this Project (all publications available publically in the Internet)
- K. Karmakar, V. Varadharajan, S. Nepal, U. Tupakula, “SDN Enabled Secure IoT Architecture”, IFIP/IEEE International Symposium on Integrated Network Management, April 2019
- U.Tupakula, V.Varadharajan, K.Karmakar, “Access Control based Dynamic Path Establishment for Securing Flows from the User Devices with different Security Clearance”, 33rd International Conference on Advanced Information Networking and Applications (AINA) March 2019
- K.K. Karmakar, V. Varadharajan, U. Tupakula, "Mitigating Attacks in Software Defined Networks" Journal of Cluster Computing, Jan 2019
- V.Varadharajan, V., K. Karmakar, K., U. Tupakula, “A policy based security architecture for software-defined networks” IEEE Transactions on Information Forensics and Security. 14, 4, p. 897-912 16 p., Apr 2019
- K. Sood, V. Varadharajan, K. Karmakar, U.Tupakula, "Analysis of Policy-based Security Management System in Software-defined Networks", IEEE Commun Letters, accepted Feb 2019
- U.Tupakula, “Design of SDN Security Architecture and its Applications”, SDN Workshop, New Zealand, Feb 2019
- V.Varadharajan, Keynote, “Security Challenges in Software Defined Networks Policy based Security Architecture ” , IEEE International Conference ISPA 2017, China 2017
This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 


